
Cybersecurity: Safeguarding the Digital Frontier
In today's digital era, cybersecurity is indispensable. As our interconnected world expands, so do the threats to our digital well-being. Cybersecurity, guarding against unauthorized access and attacks, is paramount for preserving digital integrity. Threats like phishing, malware, and social engineering loom large, leading to financial loss and data compromise. Frameworks like NIST and defense in depth strategies are pivotal, while employee education, strong passwords, and 2FA bolster security. Innovative defenses like AI, zero-trust, and blockchain are reshaping the landscape. Global collaboration is essential, transcending borders to counter evolving cyber threats. The future holds groundbreaking technologies revolutionizing cybersecurity defenses against digital adversaries in an ever-changing landscape.
Security
Introduction to Cyber security:
In an era dominated by digital technologies, the importance of cybersecurity cannot be overstated. As the world becomes increasingly interconnected, the threats to our digital lives evolve and multiply. Cybersecurity, the practice of protecting computer systems, networks, and data from unauthorized access and attacks, plays a pivotal role in ensuring the integrity, confidentiality, and availability of information in the digital realm.
The rapid expansion of the digital landscape has brought about unprecedented opportunities but has also exposed individuals, businesses, and governments to a plethora of cyber threats. One of the most prevalent threats is phishing attacks, where malicious actors attempt to deceive individuals into divulging sensitive information. These attacks often come in the form of deceptive emails or websites impersonating trusted entities. The consequences can be severe, ranging from financial loss to the compromise of personal and corporate data.
Malware infections pose another significant risk. Malicious software, including viruses, worms, trojan horses, and ransomware, can infiltrate systems, causing havoc and compromising the security of sensitive information. Ransomware has become a notorious threat, encrypting data and demanding payment for its release. The potential impact on individuals and organizations, both financially and operationally, is immense.
Social engineering is a tactic where attackers manipulate human psychology to gain access to confidential information. Whether through impersonation, pretexting, or baiting, these techniques exploit the weakest link in the security chain – people. Employee education and awareness programs are crucial in mitigating the risks associated with social engineering.
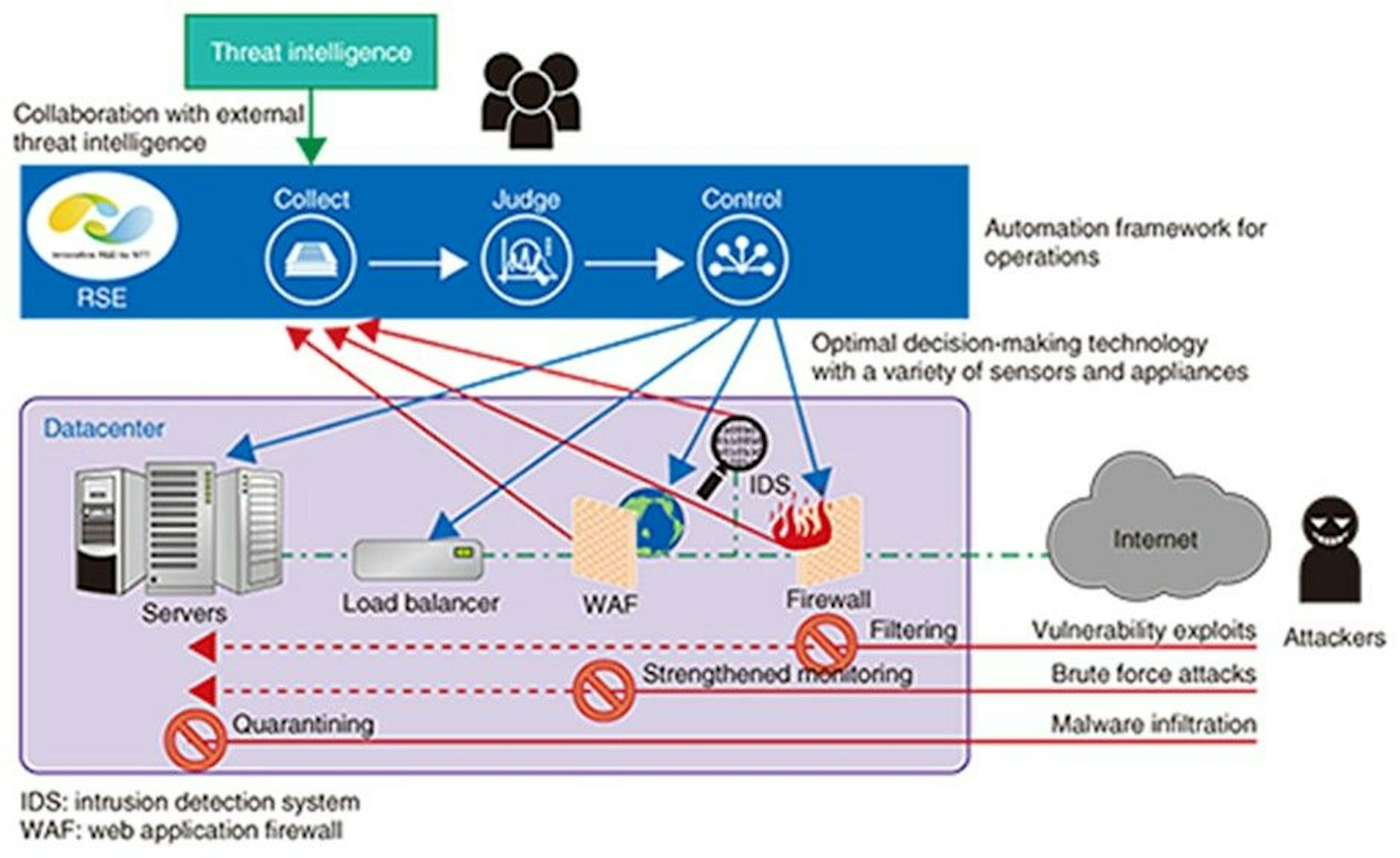
To counteract these threats, a robust cybersecurity framework is essential. The NIST Cybersecurity Framework, for example, provides a structured approach to organizing and prioritizing cybersecurity efforts. It emphasizes identifying, protecting, detecting, responding to, and recovering from cyber incidents. These principles form the foundation for an effective cybersecurity strategy.
Defense in depth is another critical concept in cybersecurity. Instead of relying on a single layer of defense, this strategy involves implementing multiple layers of security measures. Firewalls, antivirus software, intrusion detection systems, and regular software updates are among the layers that work cohesively to create a strong defense against a wide range of cyber threats.
Employee training and awareness programs are vital components of a comprehensive cybersecurity strategy. Equip employees with the knowledge to recognize and respond to potential threats. Human error is a significant contributor to cybersecurity breaches, and educating the workforce is an effective way to mitigate this risk.
The use of strong passwords and the adoption of two-factor authentication (2FA) are fundamental practices in securing access to digital accounts. Encouraging users to create unique and complex passwords, coupled with the added layer of 2FA, significantly enhances the security of online accounts.
As technology advances, so do the tactics of cybercriminals. Emerging trends in cybersecurity, such as AI-powered security, zero-trust architecture, and blockchain technology, are gaining prominence. Artificial intelligence enhances threat detection and response capabilities, while zero-trust architecture challenges the traditional notion of trust within networks, assuming that no entity should be trusted by default. Blockchain, known for its decentralized and tamper-resistant nature, is increasingly explored for securing transactions and data.
The fight against cyber threats is not confined to individual efforts. Global collaboration is imperative. Cyber threats know no borders, and coordinated international efforts are necessary to combat the increasingly sophisticated tactics employed by cybercriminals. Initiatives like information sharing, joint cybersecurity exercises, and the establishment of international standards contribute to a collective defense against global cyber threats.
We’ll delve into some of the latest technologies that are shaping the future of cybersecurity and revolutionizing the way we defend against digital threats.
1. Artificial Intelligence and Machine Learning:
Artificial Intelligence (AI) and Machine Learning (ML) are at the forefront of the cybersecurity revolution. These technologies enable systems to learn and adapt, enhancing their ability to detect and respond to new and sophisticated cyber threats. AI-driven solutions can analyze vast amounts of data in real-time, identifying patterns and anomalies that may signal an attack. From predictive analysis to behavioral analytics, AI and ML are transforming the way cybersecurity professionals approach threat detection and mitigation.

In the ever-evolving landscape of cybersecurity, staying one step ahead of malicious actors is a perpetual challenge. As cyber threats become more sophisticated, the integration of Artificial Intelligence (AI) and Machine Learning (ML) has emerged as a powerful ally in fortifying digital defenses. In this comprehensive guide, we will explore how AI and ML are revolutionizing cybersecurity, enabling more proactive, adaptive, and efficient approaches to threat detection and mitigation.
1. Advanced Threat Detection:
Traditional cybersecurity measures often struggle to keep pace with rapidly evolving threats. AI and ML empower systems to analyze vast datasets in real-time, identifying patterns and anomalies that may go unnoticed by rule-based approaches. This capability is particularly crucial in detecting advanced persistent threats (APTs) and zero-day vulnerabilities, where the attackers constantly adapt their tactics.
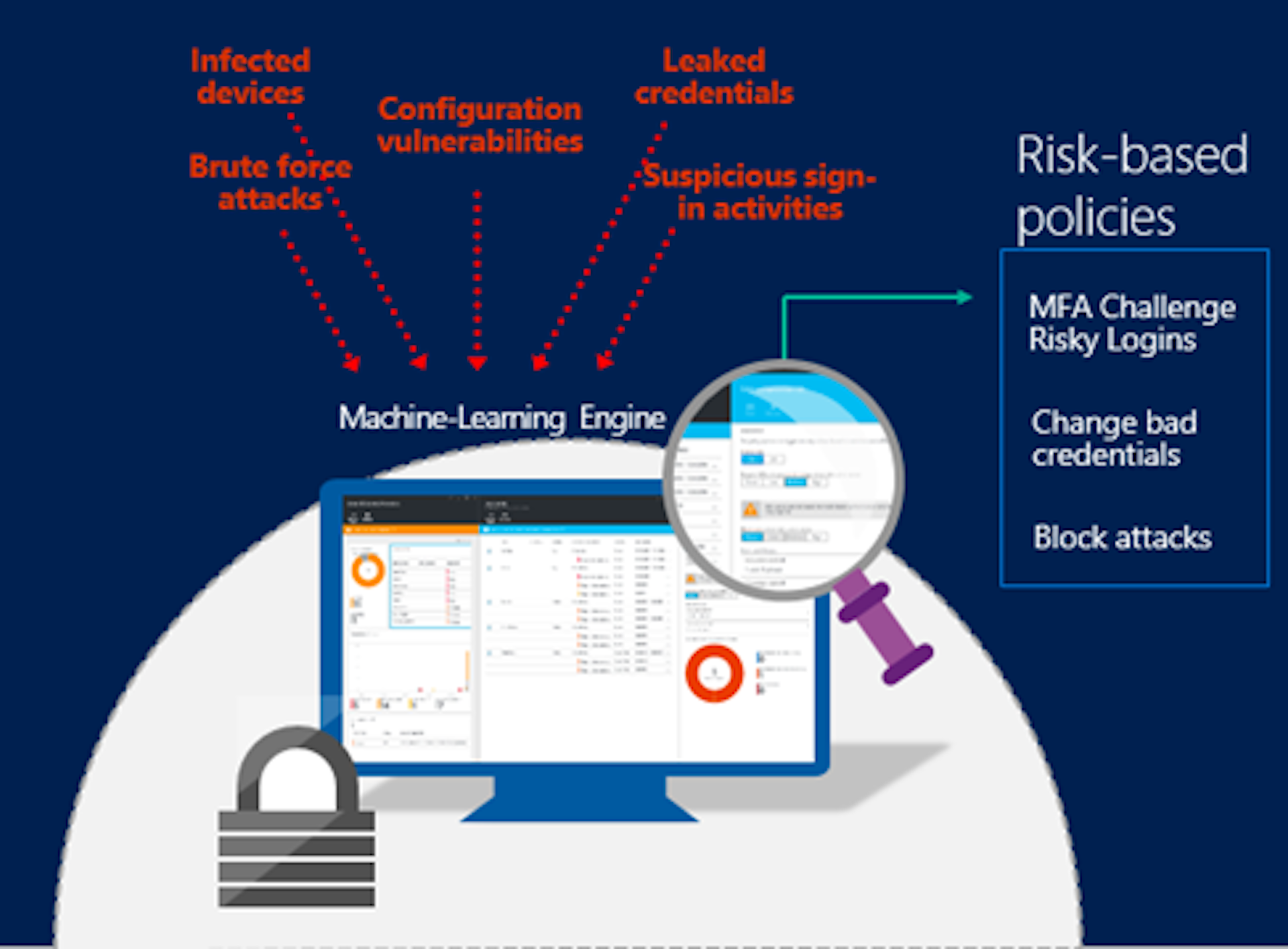
2. Behavioral Analytics:
AI and ML algorithms excel at understanding normal user behavior. By establishing baselines for individual users and systems, these technologies can quickly identify deviations that may indicate a security incident. This proactive approach enables cybersecurity professionals to respond swiftly to potential threats before they escalate.
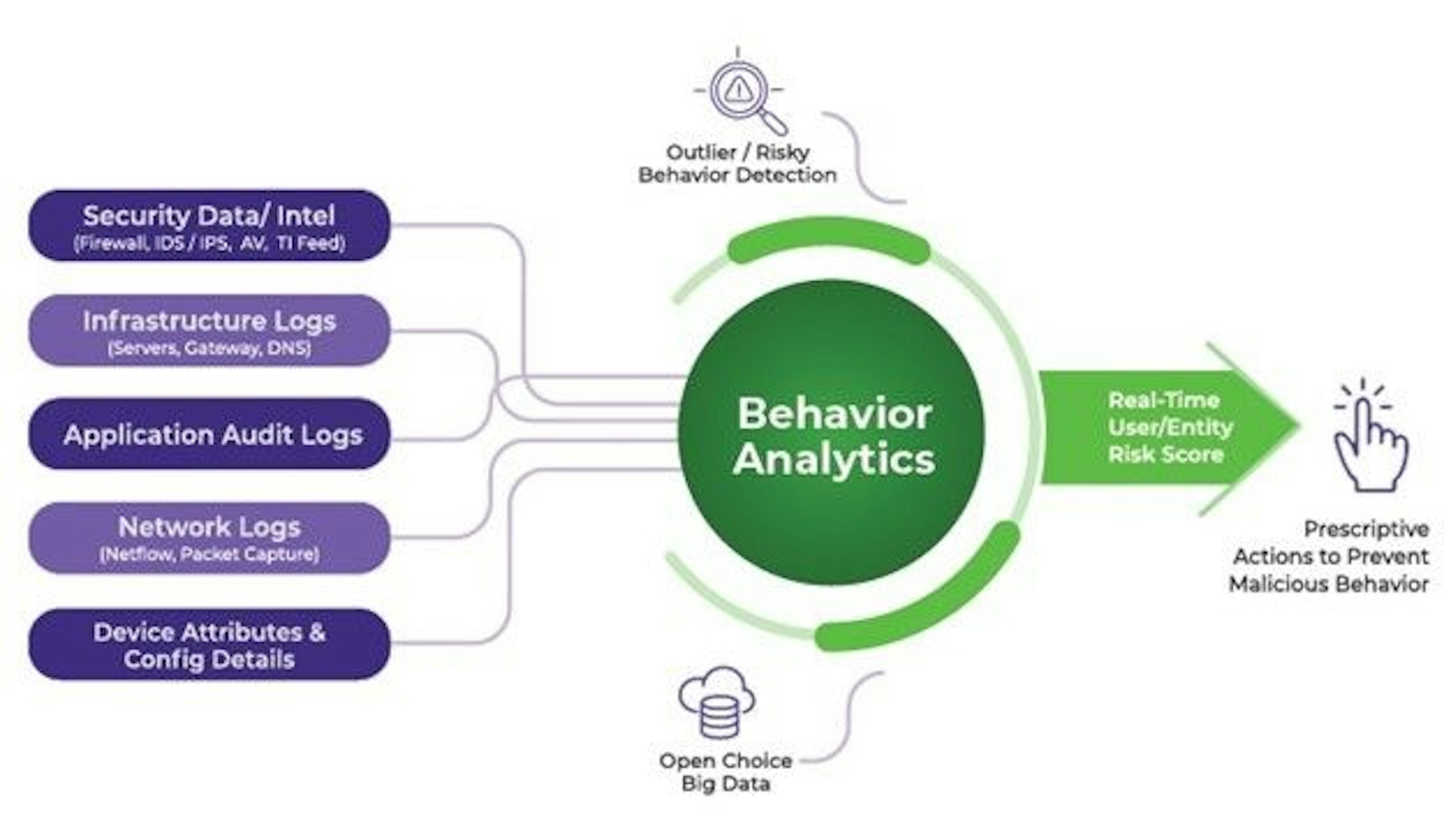
3. Automated Incident Response:
In the face of a cyberattack, time is of the essence. AI and ML-powered systems can automate incident response processes, rapidly identifying and isolating compromised systems. This not only minimizes the impact of an attack but also allows security teams to focus on more complex tasks, such as threat hunting and analysis.
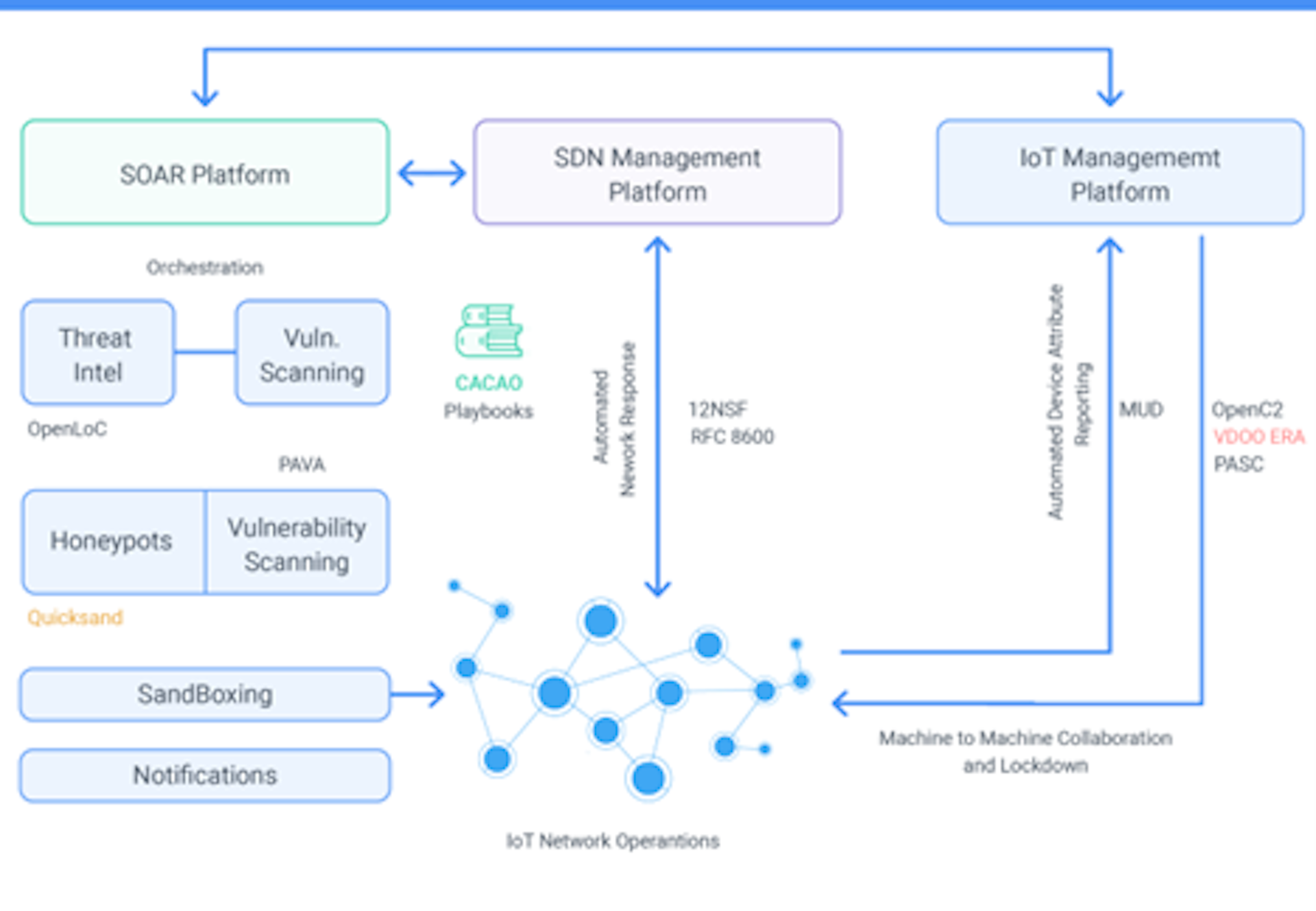
4. Predictive Analysis:
AI and ML algorithms can analyze historical data to predict potential future threats. By identifying patterns and trends, cybersecurity professionals can anticipate and prepare for emerging attack vectors. This predictive capability enhances strategic planning and resource allocation, contributing to a more proactive defense posture.
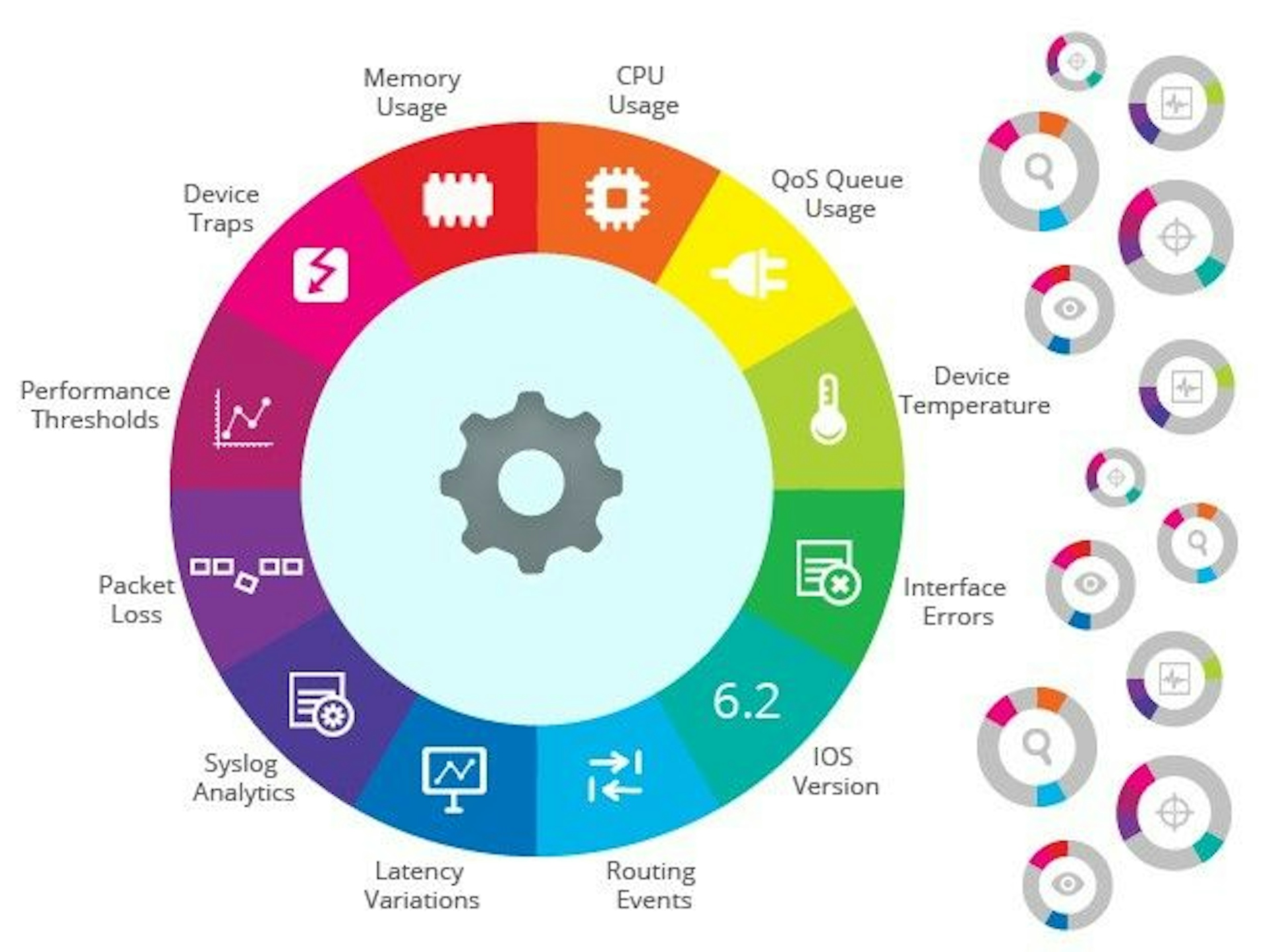
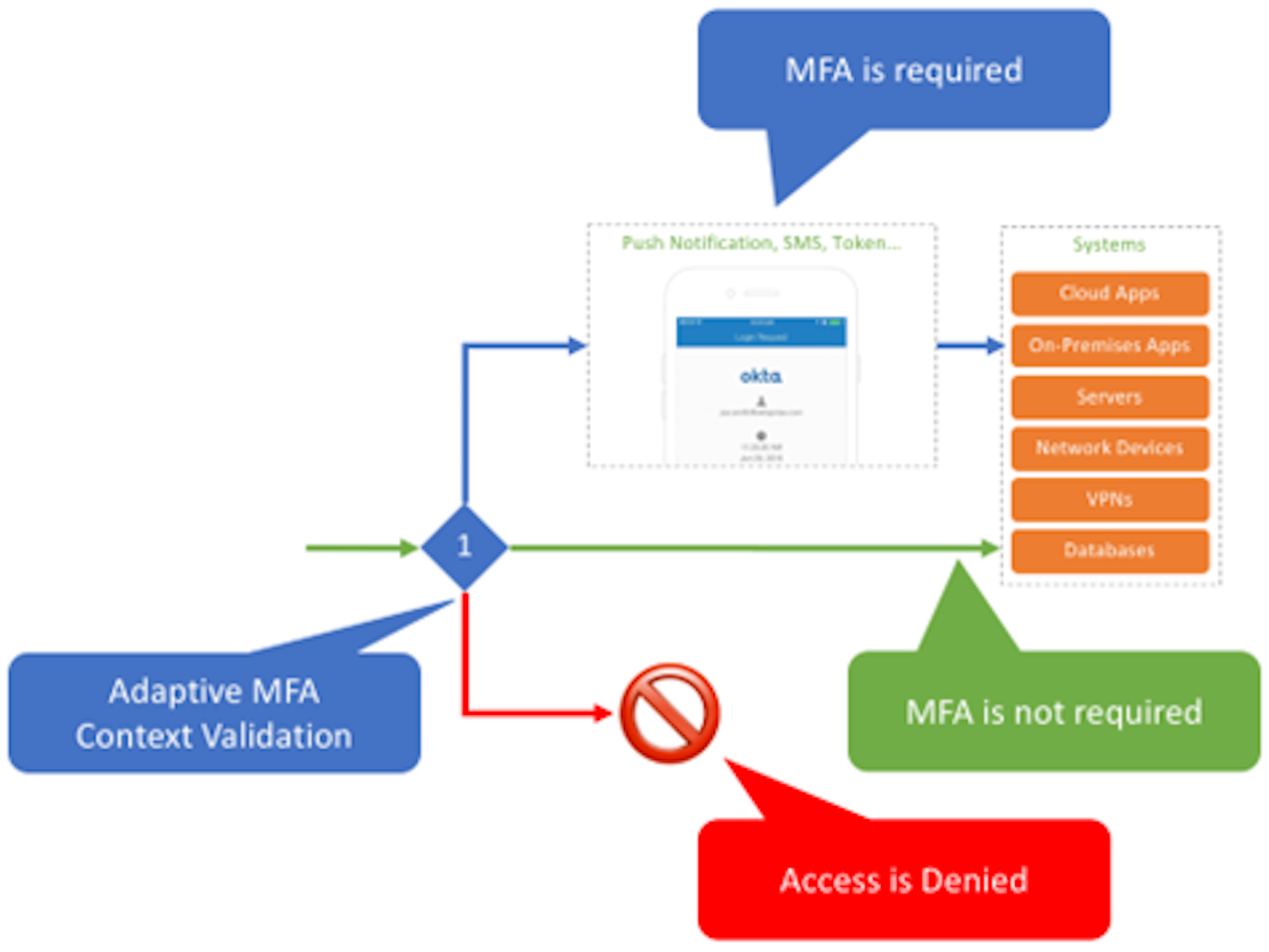
5. Adaptive Authentication:
As traditional authentication methods face increasing vulnerabilities, AI and ML enable the implementation of adaptive authentication. Systems can continuously assess user behavior and request additional verification when deviations from the norm are detected. This dynamic authentication process enhances security without sacrificing user experience.
6. Natural Language Processing for Threat Intelligence:
Natural Language Processing (NLP) capabilities in AI facilitate the analysis of vast amounts of unstructured data, including security reports, forums, and news articles. This enables cybersecurity professionals to extract valuable threat intelligence and stay informed about emerging threats in real-time.
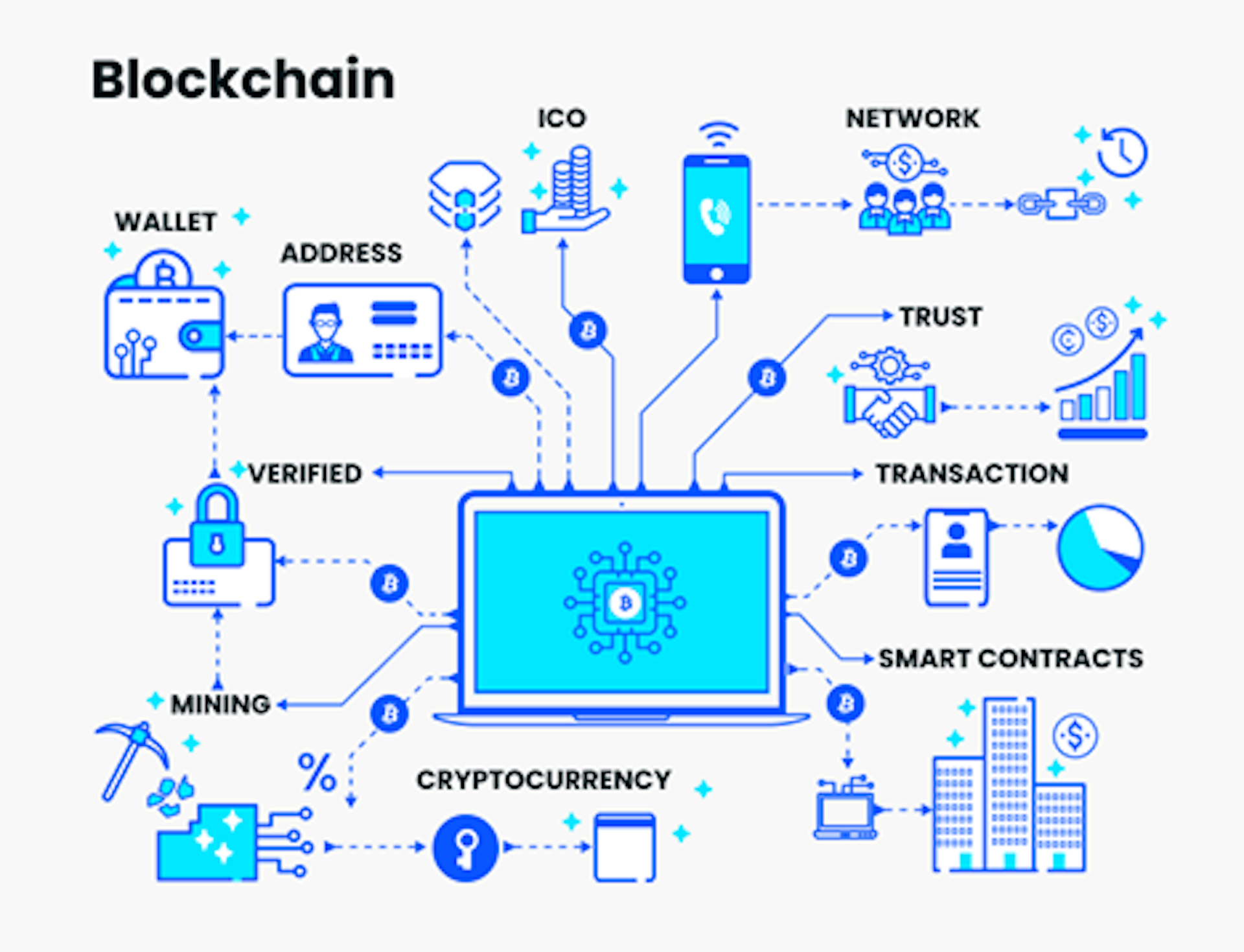
2. Blockchain Technology:
Blockchain, known for its application in cryptocurrencies, is making waves in the cybersecurity realm. Its decentralized and tamper-resistant nature makes it an attractive solution for securing transactions and data. Blockchain can be used to enhance the integrity of digital identities, secure communication channels, and provide a transparent and immutable record of security-related events.
3. Quantum-Safe Cryptography:
With the emergence of quantum computers, traditional cryptographic methods are at risk. Quantum-safe cryptography, also known as post-quantum cryptography, is designed to resist attacks from quantum computers. As quantum computing capabilities grow, implementing quantum-safe algorithms becomes crucial to maintaining the confidentiality and integrity of sensitive data.

4. Threat Intelligence Platforms:
Threat intelligence platforms aggregate and analyze data from various sources to provide actionable insights into potential cyber threats. These platforms help cybersecurity professionals make informed decisions by understanding the tactics, techniques, and procedures employed by threat actors. As cyber threats become more sophisticated, the need for comprehensive threat intelligence becomes paramount.
Conclusion:
In conclusion, cybersecurity is a dynamic and ever-evolving field that requires continuous adaptation to the changing digital landscape. Individuals, businesses, and governments must recognize the severity of cyber threats and take proactive measures to secure their digital assets. From implementing robust defense mechanisms and fostering a culture of cybersecurity awareness to embracing emerging technologies, the quest for a secure digital future demands collaboration, innovation, and a steadfast commitment to protecting the digital frontier.