Basics of MITRE ATT&CK Framework
Cyber threats are out there, whether in the form of malware or threat actors. As defenders, observing and adapting to these threats is vital. This process begins by asking tough questions, such as, how will these adversaries target us, and what will they do after they get access to our networks? This is where ATT&CK comes in. ATT&CK is our knowledge base of adversary behaviours based on real-world observations.
Amar DAugust 30, 2023

ATT&CK is primarily informed by what has been seen in operational use by the broader community. The matrix view in ATT&CK captures relationships between tactics, techniques, and sub-techniques.
What are the basic components of MITRE ATT&CK?
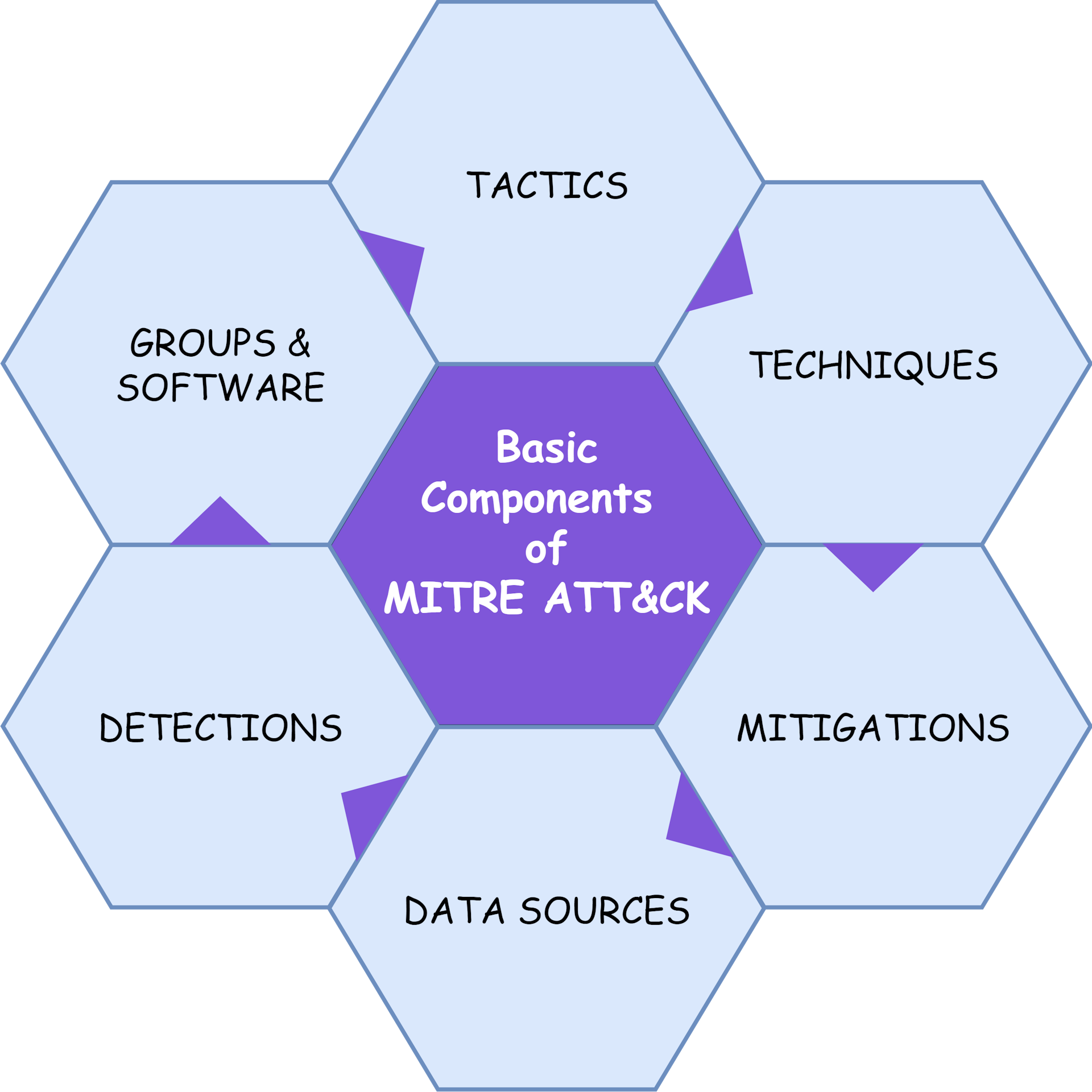
Each Matrix is centred around a specific technology domain. Each ATT&CK matrix is not completely different from the other one. Whether it is matrices or tactics or techniques everything in the ATT&CK can be seen from three perspectives i.e., enterprise, mobile and ICS. Each matrix focuses on a specific technology domain or platform.
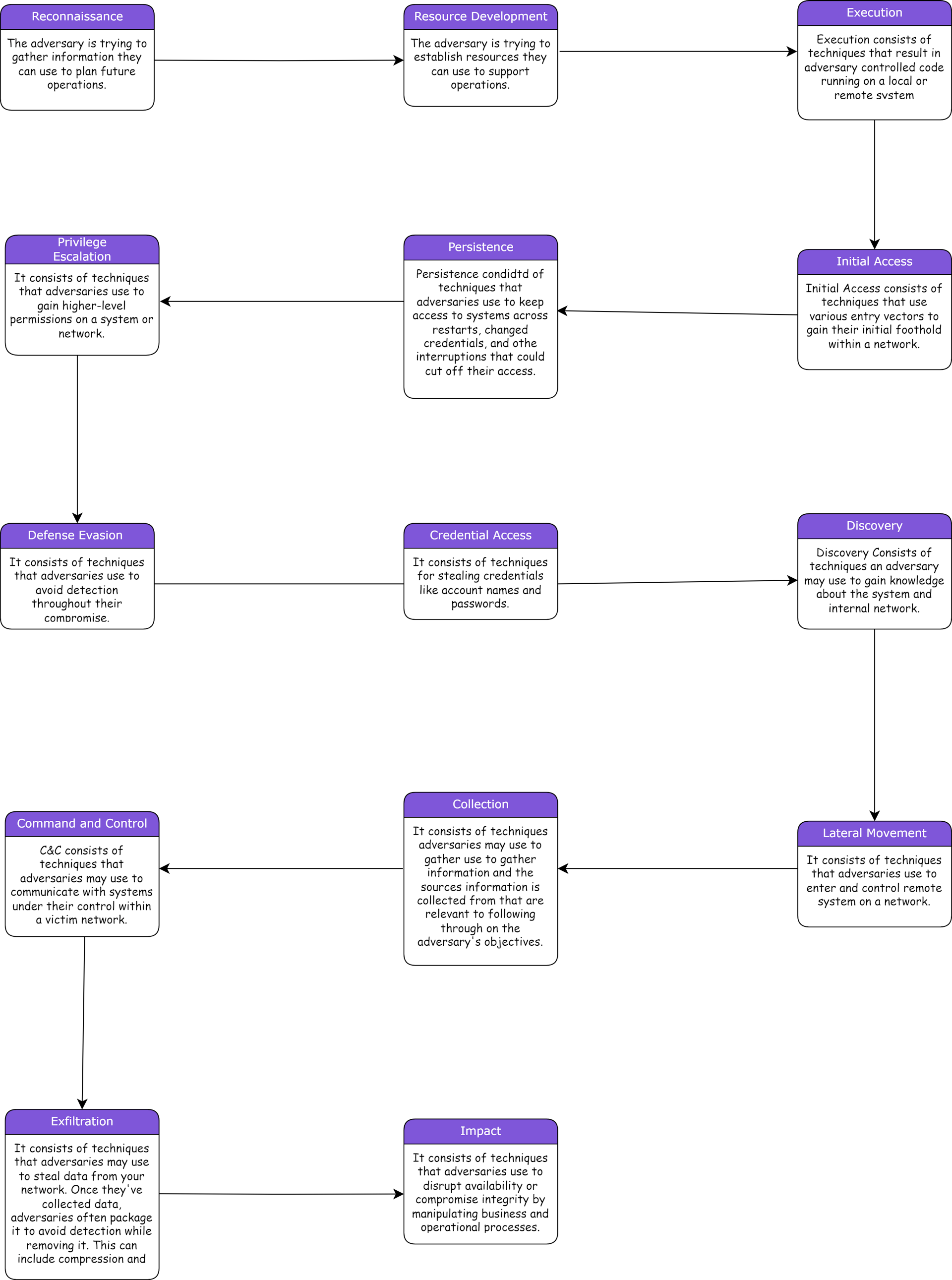
TACTICS
- It is the tactical adversary's goal during an attack.
- It gives us WHY an adversary performs each action.
- The list of tactics may differ across technology domains but are relatively static over time.
- Each tactic is assigned an ID as well as a short and longer description.
- An ATT&CK TACTIC is an intermediate objective of the adversary.
TECHNIQUES
- Means by which adversaries achieve their tactical goals (adversary Perspective). HOW an adversary performs each action.
- The list of techniques may differ across platforms but may grow and evolve.
- Sub-Technique TIDs are just extensions of their parent's TID.
- Syntax for IDs for Technique is T#### and Sub-technique is T####. ### (must be under a technique).
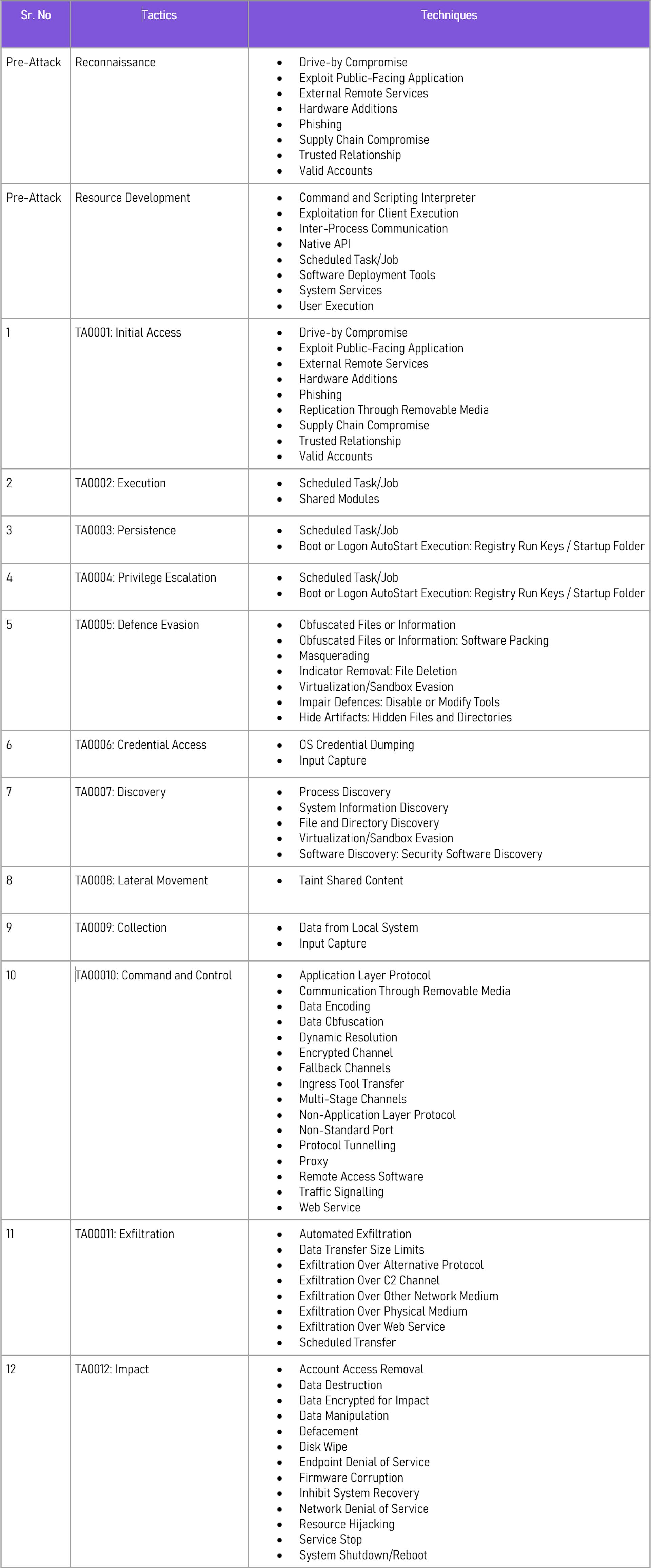
Following are the TTPs (tactics, techniques, and procedures) based on MITRE Attack Framework:
MITIGATIONS
- These are configurations, tools, or processes that can prevent a technique from working or having the desired outcome for an adversary.
- This is intended to allow you to take action such as changing a policy or deploying a tool.
- ATT&CK Mitigations are recommendations for how to prevent the successful execution of specific adversary behaviours.
- Mitigations are mapped to specific techniques and are displayed on those pages as well as on their own mitigations page.
Data Sources
- It gives us WHERE to collect data.
- It provides a source of information collected by a sensor or logging system.
- Historically, ATT&CK use data source values to point defenders to where they need to collect information.
DETECTIONS
- It gives us HOW to interpret collected data.
- It is useful to identify a technique that has been used by an adversary.
GROUPS AND SOFTWARE
- ATT&CK defined groups as related intrusion activity that are tracked by a common name.
- Software is defined as a tool or malware used by an adversary during intrusions. Some entries have multiple names.
- Some groups and software have multiple names associated with similar activities.
- ATT&CK Groups represent named clusters of intrusion activity, whereas Software represents the tools/malware used by these actors.
ATT&CK is a Team Effort
- The framework is collaboratively built from:
- Publicly available reporting and documentation
- Insights and feedback
- Citable contributions from the global community.
- Citable contributions from the global community.
- The MITRE ATT&CK team curates and maintains this collective knowledge.
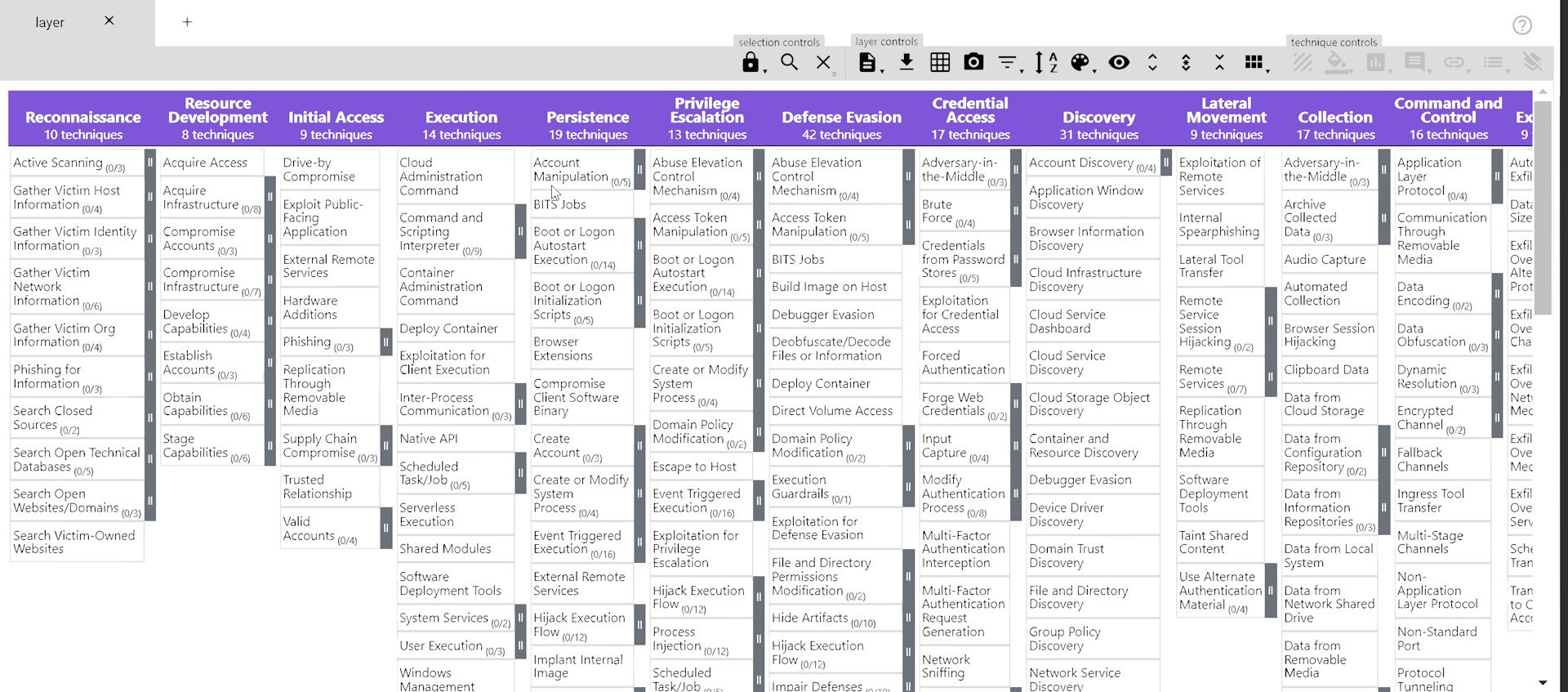
ATT&CK Navigator
- It is designed to provide basic navigation and annotation of ATT&CK matrices. We can select each cell or technique in the Navigator. There’s also a control panel at the top, files to perform various other actions, such as selecting techniques based on their mappings to groups, software, or mitigations.
- We can also use these controls to add colour to various other annotations to selected cells. Once done, we can export those layers into JSON, Excel, or image formats. The Attack Navigator allows us to create new layers, as well as build on or open existing layers.
The ATT&CK Mapping process includes the following process:
Step1: FIND THE BEHAVIOR
- Look for what the adversary or software does during the steps of the compromise.
- Focus on pre-compromise, initial compromise, and post-compromise details.
- Identify how the adversary earned initial access and how they moved through the compromise of the victim network/system.
- Look for the verbs in the narrative reporting to identify adversary behaviors, such as:
- Used email attachments,
- Create scheduled tasks, and
- Installed tools.
Step2: RESEARCH THE BEHAVIOR
- Perform additional research on unfamiliar adversary/software behaviors
- Examine details about network protocols that were used including their OSI layer/capabilities, assigned port number, associated service, and any potential vulnerabilities that can be leveraged by adversaries.
- Collaborate within your organization (defenders/red teamers)
- Leverage external resources.
- Understanding core behaviors help with the next steps and enhances analytic skills.
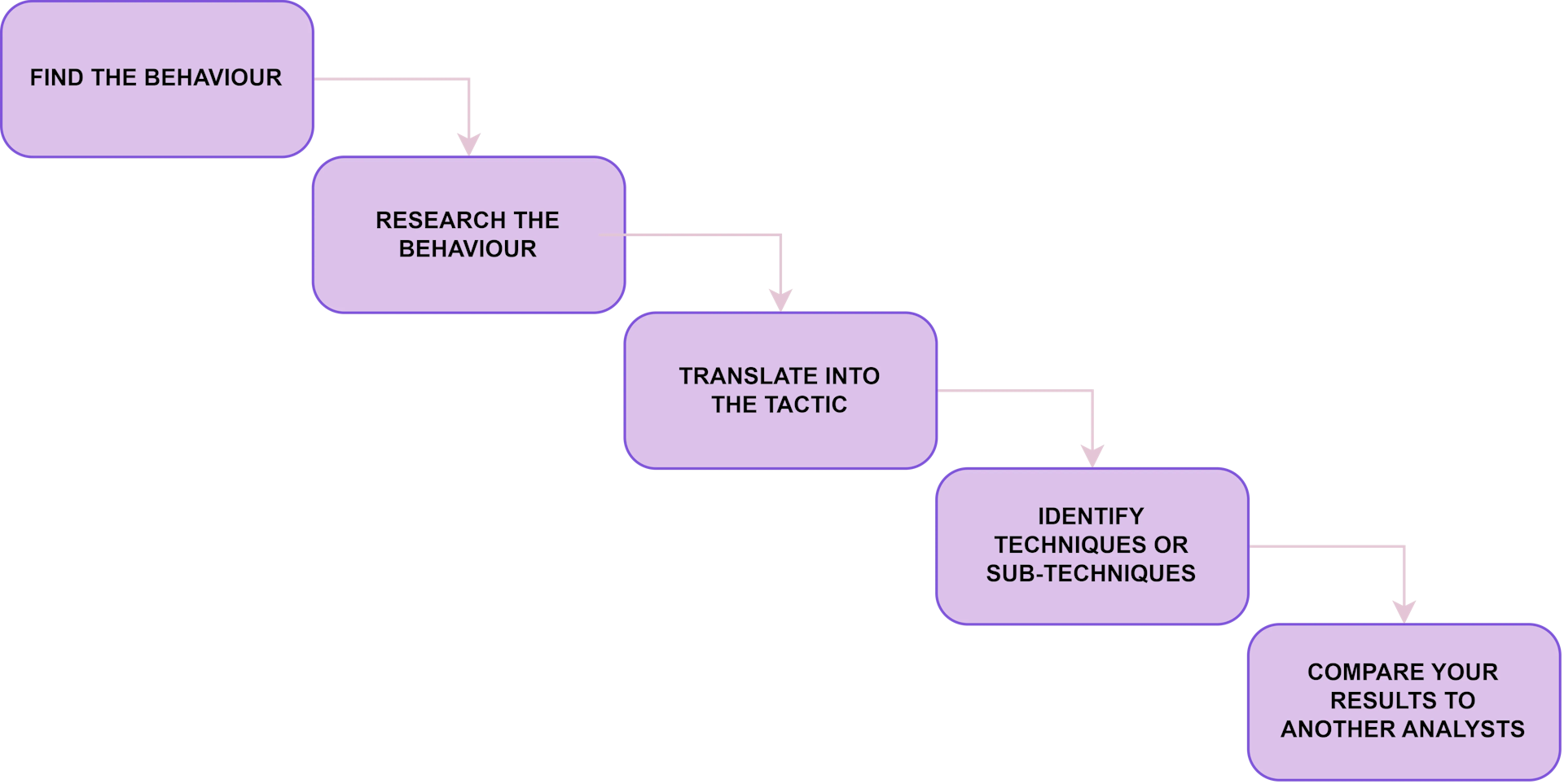
Step3: TRANSLATE THE BEHAVIOR INTO A TACTIC
The following flow chart gives us the behaviors for each of the Tactic:
Step4: IDENTIFY WHAT TECHNIQUE & SUB-TECHNIQUE APPLIES
- Some techniques help facilitate more than one tactic, and this is reflected throughout ATT&CK.
- For example- Hijack Execution Flow: DLL Side-Loading fails under persistence, Privilege Escalation, Defence Evasion.
- Not all adversary behaviors can or should be used as a basis for alerting or providing data to an analyst because not every behavior that can be mapped is malicious.
- Context is key in assessing the circumstances around the behaviour and can help identify if it's malicious in nature.
- Key strategies for this step are as follows:
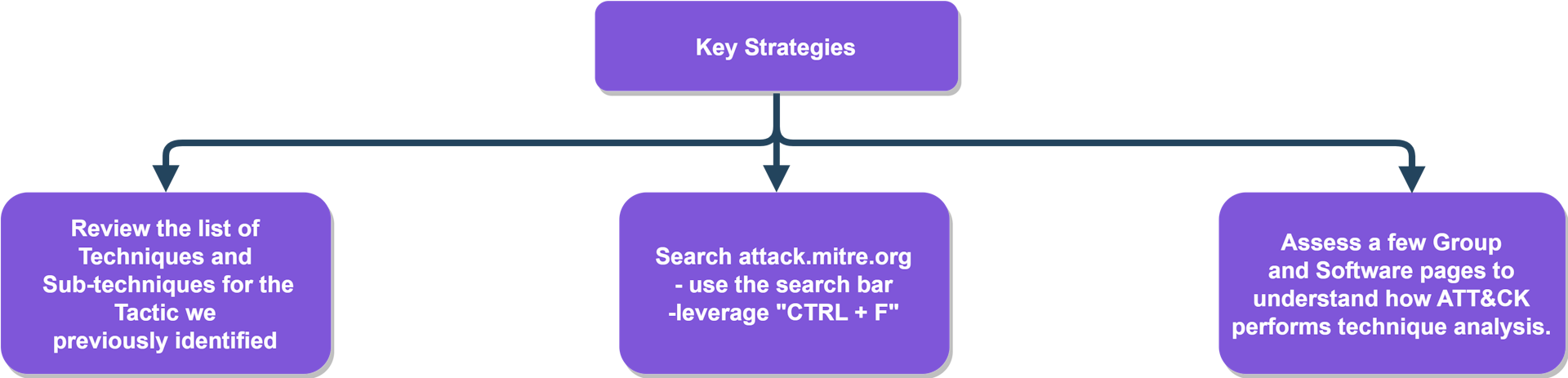
Step5: COMPARE YOUR RESULTS
- This can help hedge against analyst biases. So, we will be getting into a number of different reasons why different analysts might come up with different answers.
- But everyone has a different set of experiences and background that they’re drawing upon as they do intelligence analysis.
- So where one analyst may see not application layer protocol, and another may see custom command and control protocol.