Enhancing Security with Multi-Factor Authentication: A Powerful Defence Against Cyber Threats
In the digital age, data breaches are prevalent, making strong security measures essential. Multi-Factor Authentication (MFA) is a powerful method to protect sensitive information. MFA requires multiple forms of identification, adding an extra layer of security. In this post, we'll explore MFA, its benefits, and widespread adoption.
Security
Introduction
In today's digital age, where data breaches and cyber threats are increasingly prevalent, it has become imperative for individuals and organizations to strengthen their security measures. One of the most effective methods to bolster authentication and protect sensitive information is through Multi-Factor Authentication (MFA). In order to gain access to a network, application, or other digital asset that isn't normally accessible to the public, a user must provide more than one form of identity identification, which is known as multi-factor authentication, or MFA. MFA adds an additional layer of security by combining multiple verification factors, making it significantly more challenging for unauthorized individuals to gain access. In this blog post, we will explore the concept of Multi-Factor Authentication, its benefits, and its widespread implementation across various sectors.
Understanding Multi-Factor Authentication (MFA)
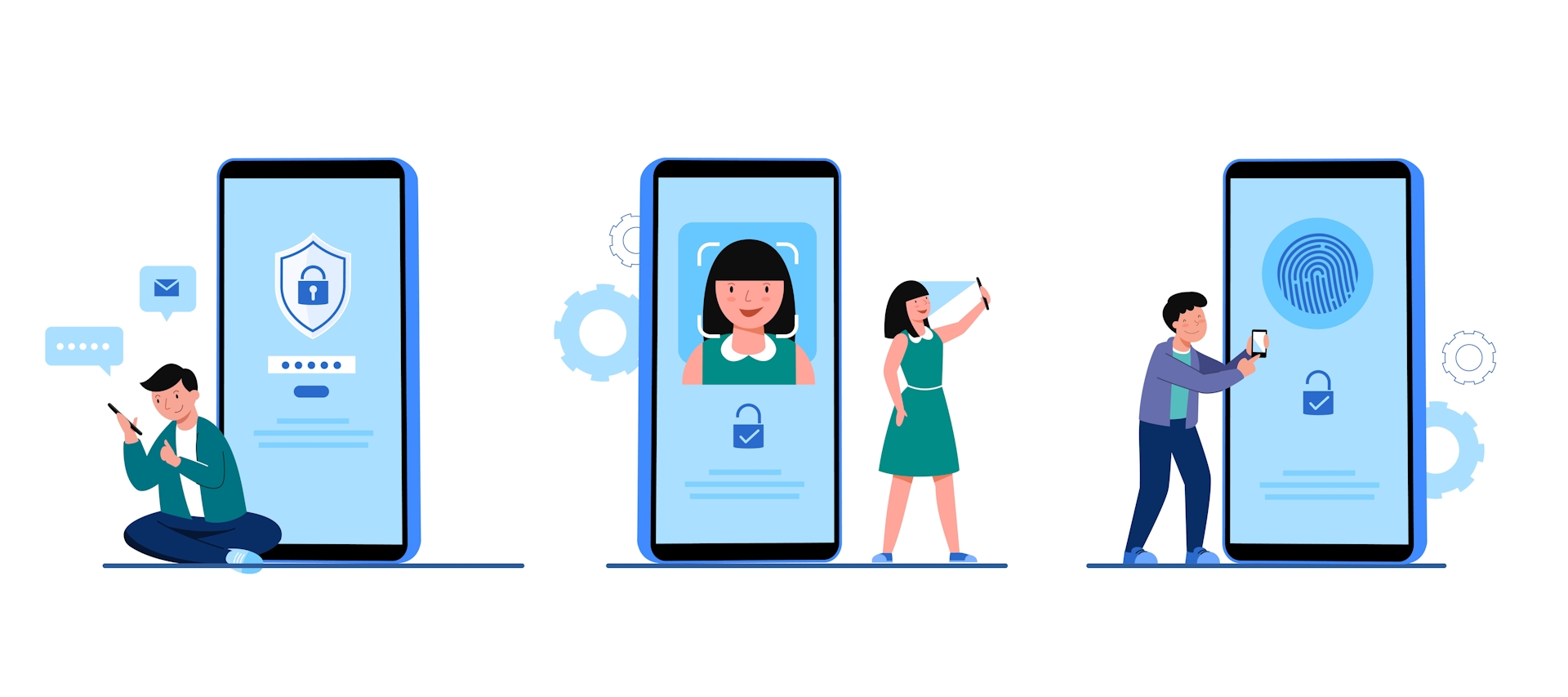
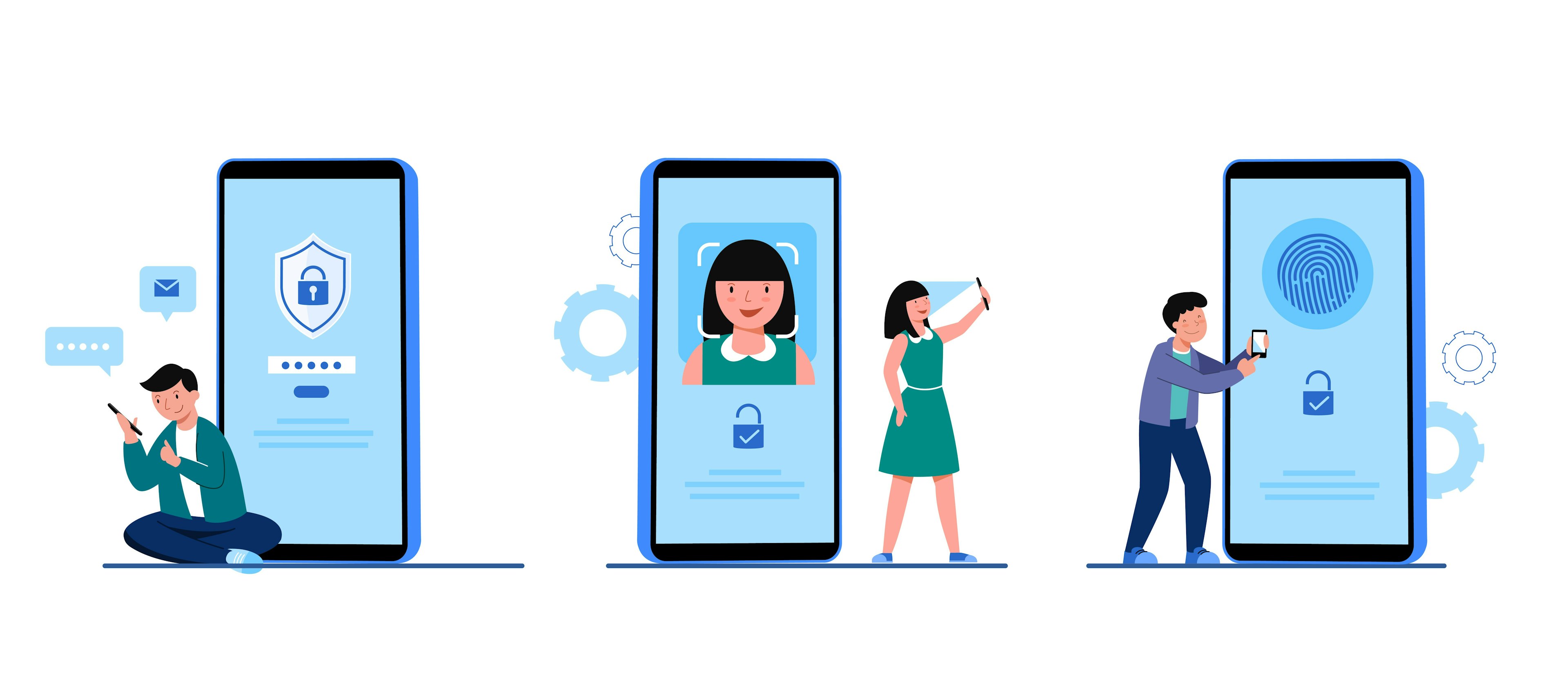
Multi-Factor Authentication, as the name suggests, involves the use of multiple factors or credentials to verify a user's identity before granting access to a system, account, or application. Traditionally, authentication relied solely on a single factor, typically a username and password. However, this technique has validated to be susceptible to numerous cyber-attacks, such as phishing, credential stuffing, and password guessing. Single-factor authentication is a challenge because there is little to no opportunity for error with only one line of defence. A strong, one-of-a-kind alphanumeric password can nevertheless be made public using a variety of methods, including brute force assaults, key loggers, phishing scams, social engineering, and malware implantation. Additionally, studies have shown that when left to their own devices, people are notoriously bad at managing passwords. For example, nearly one in every 200 passwords, or roughly three-fourths of the global workforce, simply reuse the same password across multiple accounts.
MFA requires users to supply extra data or credentials in order to access an account. Therefore, it's improbable that an attacker will also be able to steal or compromise the other authentication factors needed for MFA, even if they do succeed in stealing passwords. Because of this, MFA can deter fraudsters and effectively defend against a variety of threats. It aims to cope with these vulnerabilities by incorporating two or more authentication factors from different categories. These categories typically include:
- Something you know: The customer is required to provide information that should only be known by them, such as a password, PIN, or the solutions to security questions, as part of this component. User scenarios that are typical include the following:
- Using a debit card to pay for groceries and entering a PIN.
- Before gaining access to a network, downloading a VPN client with a current digital certificate and logging in.
- Giving information to get system access, such as your mother's maiden name or a past address.
- Something you have: A tangible device must be owned in order to satisfy this requirement; examples include a smartphone, smart card, or hardware token that produces one-time passwords (OTP).
- Something you are: This element is based on the user's particular biological qualities or attributes, such as voice recognition, fingerprint recognition, retina/iris recognition, or facial recognition.
The following are examples of typical inherence factor scenarios:
- Accessing a smartphone with a fingerprint or facial recognition.
- Using a digital signature at a checkout in a store.
- Criminal identification via earlobe geometry.
- Somewhere you are: This element considers the user's proximity to the system or the network they are using to access it, generally using IP geolocation or GPS coordinates.
When these elements are combined, MFA provides an extra degree of security against unauthorized access and significantly lowers the chance of compromised money possessed. As a result, even if a malicious actor is successful in obtaining the correct password, they will still require a separate authentication method, which may be much harder to obtain. A Google investigation found that the additional verification step was successful in thwarting 66% of targeted attacks, 99% of bulk phishing attacks, and 100% of automated bots. Microsoft promises that MFA can prevent up to 99.9% of attacks, despite the fact that its cloud services see an average of 300 million unauthorized sign-in attempts per day.
Benefits of Multi-Factor Authentication

- Enhanced Security: MFA significantly reduces the risk of unauthorized access, as despite the fact that one element is compromised, the attacker would nonetheless want to skip additional authentication elements.
- Stronger Protection Against Phishing: Since MFA involves a physical element or biometric factor, it will become a good deal tougher for attackers to trick users into revealing their credentials through phishing attempts.
- Mitigation of Credential Stuffing Attacks: With MFA, even if an attacker possesses a valid username and password combination (likely obtained from a data breach), they would still be unable to access the account without the additional verification factors.
- Compliance with Regulatory Standards: Many regulatory frameworks and data protection laws now require organizations to implement stronger authentication methods. MFA helps meet these compliance requirements by adding an extra layer of security.
- Flexibility and User Experience: MFA can be implemented across various platforms and applications, providing users with flexibility in choosing the most convenient authentication method. It also eliminates the need to remember multiple complex passwords.
- MFA is successful at thwarting ransomware attacks in addition to conventional hacks. When an attacker obtains account credentials, a ransomware attack begins. With MFA, however, the attackers lack the extra information needed to access the target account. This blocks the attack and keeps them out of the system.
- Furthermore, when IT administrators start receiving unusual MFA authorization requests, any unauthorised login attempts will trigger an alert. Then, they can act right away to keep these assailants out. Organisations may fend off ransomware attacks and shield themselves from pricey extortion demands by deploying MFA. Context-aware, adaptive MFA options, such as One Login's Smart Factor Authentication, are quite useful in this regard. To modify the amount of authentication factors required to log in, Smart Factor Authentication assesses a wide range of inputs, including user location, device, and activity. It also evaluates the degree of risk associated with each login and dynamically modifies the authentication requirements in real time. Thus, it consistently protects the company against ransomware threats.
Implementation of Multi-Factor Authentication
MFA has become increasingly prevalent across numerous sectors, including banking, healthcare, e-commerce, government institutions, and online services. The implementation of MFA typically involves the following steps:
- Selection of Authentication Factors: Organizations must determine which authentication factors are most suitable for their specific needs. This could include a combination of passwords, OTPs, biometrics, or location-based factors.
- Integration and Configuration: Organizations need to integrate MFA into their existing authentication systems, applications, or websites. This may involve using pre-built MFA solutions or developing custom integrations.
- User Enrolment and Education: Organizations should educate users about the benefits of MFA and guide them through the enrolment process. Clear instructions and user-friendly interfaces can encourage user adoption.
- Continuous Monitoring and Updates: MFA systems should be regularly monitored for potential vulnerabilities or weaknesses. Software updates and patches should be applied promptly to ensure the highest level of security.
Conclusion
In an era wherein cyber threats maintain to conform, it’s far vital to adopt sturdy security measures to shield touchy records. Multi-Factor Authentication presents an effective answer through including a further layer of safety and making it notably more difficult for attackers to benefit unauthorized access. By incorporating more than one authentication factors, businesses can mitigate the dangers related to vulnerable or compromised credentials, phishing attacks, and different protection vulnerabilities. Implementing MFA now not only safeguards facts however additionally instils confidence in users, reinforcing trust in virtual platforms and offerings.