Understanding Ports and Protocols
Alright, time to get to the heart of the matter: ports and protocols. I know it might sound nautical, but I promise, it's all about computers and networks.
Muhasib BhatSeptember 28, 2023

What are Ports?
Imagine a massive skyscraper stretching high into the sky. Its facade is covered in an intricate grid of countless doors, each one labeled with a number. As you approach, you realize that each door leads to a different room, each hosting a unique activity. These doors, in the realm of networking, are akin to “ports” – gateways to distinct services and applications. There are diverse ports for distinct purposes – one for sending emails, another for browsing the web, and so on. Pretty neat, huh?
Common Network Protocols
In the realm of networking, understanding protocols is akin to grasping the fundamental rules that govern the flow of data through ports, which serve as the gateways to various services.
Ever surfed your favorite website? Of course, you have! When you visit a beloved website, your computer relies on a protocol known as HTTP for a seamless interaction. Likewise, the transmission of emails often engages the SMTP protocol. These protocols serve as the bedrock, ensuring the precise and reliable delivery of data to its intended destination.
Now, let’s delve into a pivotal distinction: TCP versus UDP.
TCP vs. UDP
Can't forget about TCP and UDP – the big players. Picture TCP as a meticulous postman ensuring every letter arrives in sequence, while UDP rushes to deliver quickly, sometimes mixing things up a tad.
TCP (Transmission Control Protocol): Reliable, orderly, a bit slower – like a tracked package.
UDP (User Datagram Protocol): Fast, furious, less concerned about order – ideal for speedy tasks, like video streaming.
So, What's the Big Deal?
Understanding ports and protocols is like knowing a secret handshake in a club. It equips us, ethical hackers, to approach systems strategically, identify targets, and assess vulnerabilities.
Port Numbers and Services
With ports and protocols explained, let's dig deeper. All these doors (ports) need labels, right? Let's uncover how port numbers work and the services tied to them.
Well-Known Ports (0-1023)
Just like renowned rockstars, some ports are universally recognized. These ports are the VIP section in networking. You've likely encountered a few.
Port 80: That's where HTTP magic unfolds – web browsing hub.
Port 443: Enter HTTPS, secure browsing's domain.
Port 21: FTP's realm, the file transfer core.
Registered Ports (1024-49151)
Next up, registered ports. Think of them as up-and-coming networking talents. Not quite VIP, but they're essential and reserved for specific tasks.
Port 3306: Home of MySQL.
Dynamic or Private Ports (49152-65535)
Lastly, dynamic or private ports – the wild west. Unregulated and used for temporary or private services, they're unpredictable, like plot twists in a thriller.
Similar to knowing the best local coffee shops, grasping port numbers and services gives ethical hackers an edge. It directs actions, clarifies observations, and sharpens focus for deeper probing.
Protocols and Ethical Hacking

HTTP/HTTPS
Remember HTTP and HTTPS from the famous ports? They're not just for browsing. Ethical hacking benefits from them, revealing valuable insights. HTTP, unencrypted, can yield treasure while sniffing network traffic. HTTPS, encrypted, still offers system activity clues.
FTP
Next, FTP – the File Transfer Protocol. The internet's delivery truck, moving files around. Watch closely, as it might unveil vulnerabilities when people transfer sensitive files carelessly.
SSH
Now, SSH, Secure Shell – the secret passage for secure communication. Yet, secrets can have weak spots. Keys (or passwords) might be guessable, or outdated versions vulnerable.
Telnet
Telnet, a bit old-school, like a classic rock song. It remotely controls systems, but it's insecure. Spotting Telnet might uncover a weak point.
SMTP
Last but not least, SMTP – Simple Mail Transfer Protocol. The internet's post office, shuttling emails. As ethical hackers, monitoring SMTP traffic could unveil poorly protected content or phishing attempts.
Protocols are akin to languages. The more you comprehend, the better you communicate. In ethical hacking, knowing protocols enhances system interaction, vulnerability detection, and effective security measures.
Ethical hacking's charm lies in every protocol, service, and port being a potential entry point. It's an endless puzzle, and you're the master solver.
Port Scanning Techniques

Time to roll up our sleeves! We've touched on ports and protocols, but how do we uncover open doors? Enter the world of port scanning – an essential ethical hacking skill.
The Role of Port Scanning
Imagine facing a wall with countless doors – some open, some closed. Your task? Locate the open ones. That's port scanning. A vital part of ethical hacking, it uncovers potential entry points into systems.
Types of Port Scans
Not all port scans are the same. We've got an array of techniques, each with strengths and weaknesses.
TCP Connect Scan: Classic door-knocking. Like checking if someone's home. Reliable but conspicuous.
Stealth Scan (SYN scan): Sneakier. Like leaving a note and vanishing before anyone spots you. Swift, quiet, but not always precise.
UDP Scan: Special knock for UDP doors, as they respond differently. Tricky but vital for uncovering UDP services.
Tools and Utilities
Manual scans for all these ports? Nope! We've got tools. Meet Nmap, the rock star of port scanning. Powerful, versatile, and free!
Ready for Action
Port scanning is like a treasure hunt. With these techniques and tools, you're well-equipped to explore. But remember, ethical and legal scanning is key.
Common Ports and Protocols
Now, let's dive into a comprehensive table listing common port numbers, their corresponding protocols, and typical uses.
Transport Layer Protocols
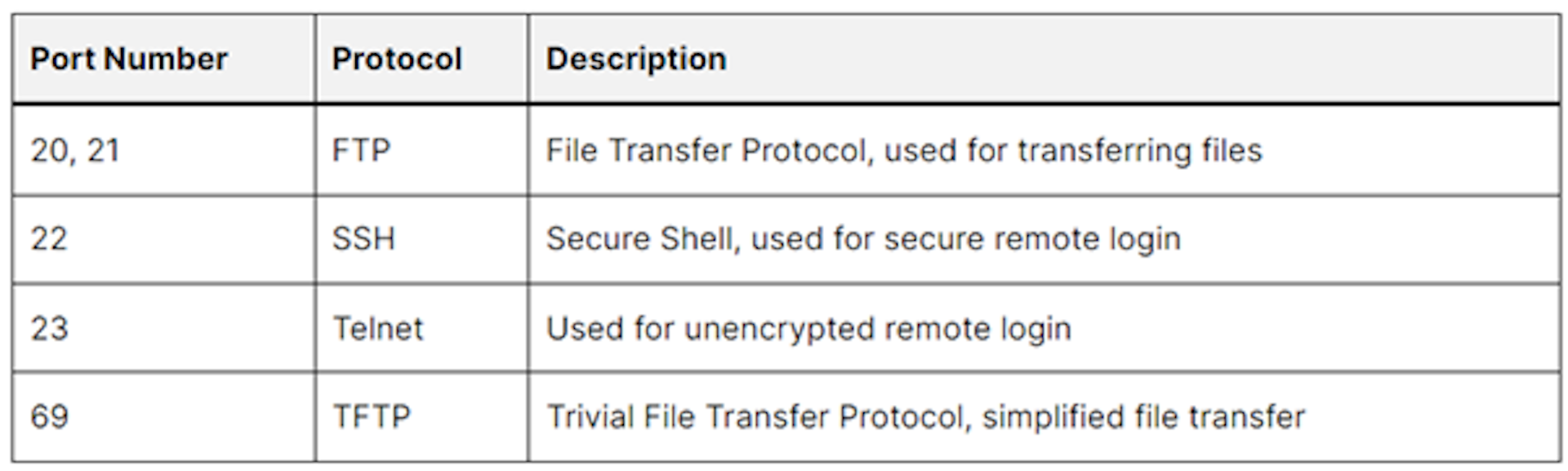
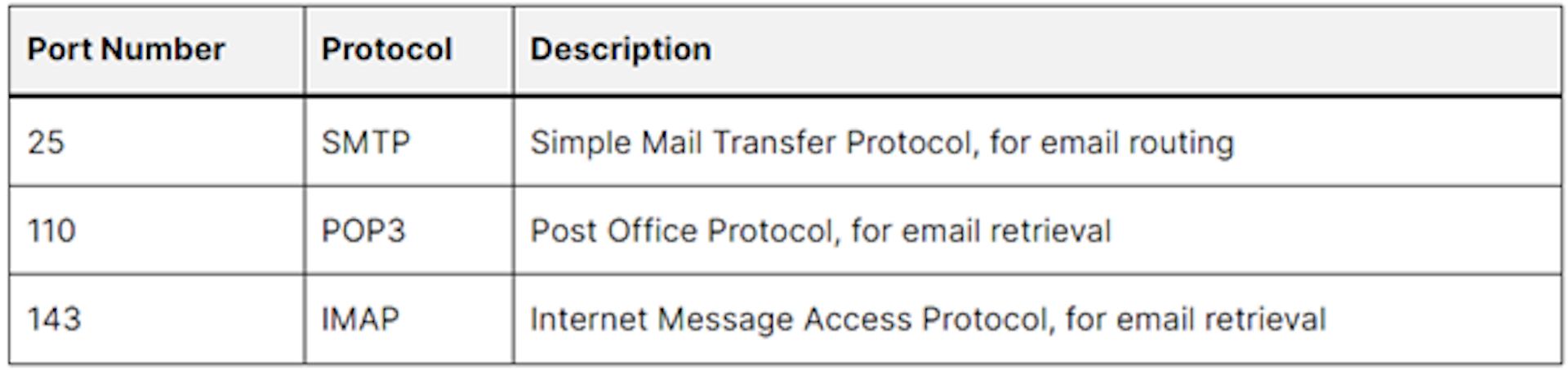
Email Protocols
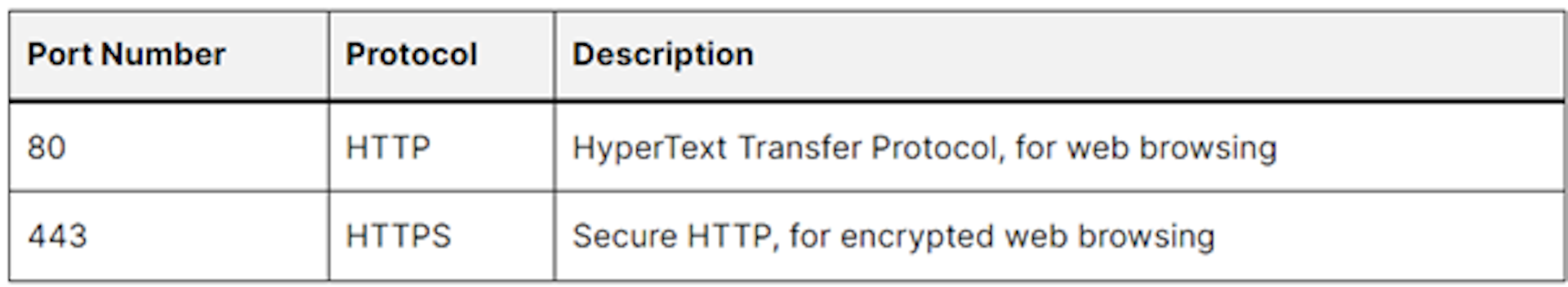
Web Protocols
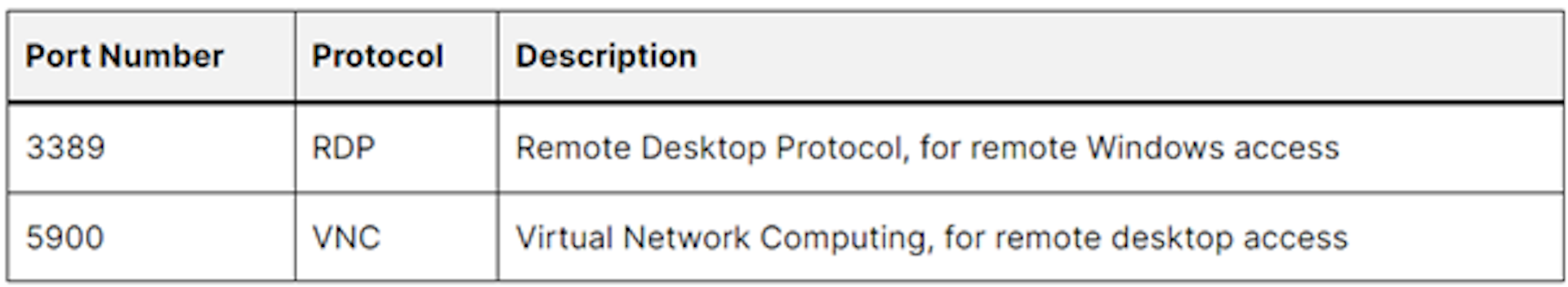
Remote Access Protocols
DNS and Directory Services
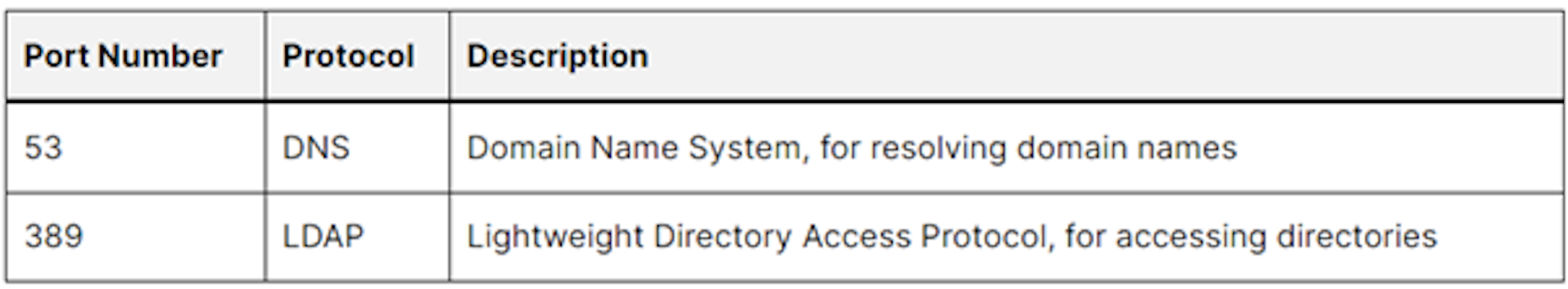
Network Management Protocols
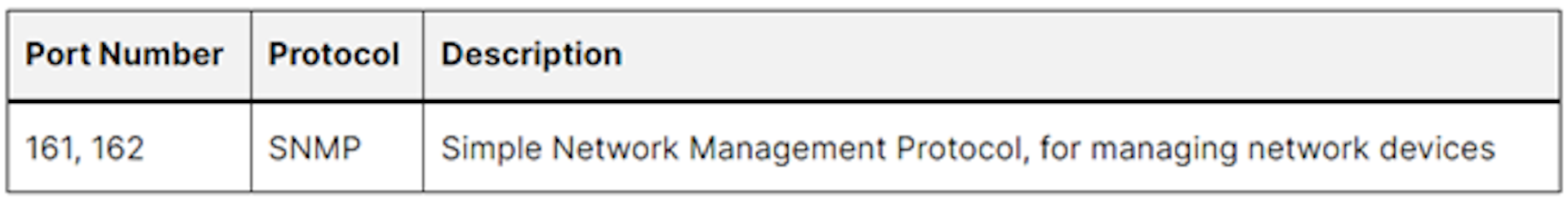
VPN and Tunnelling Protocols
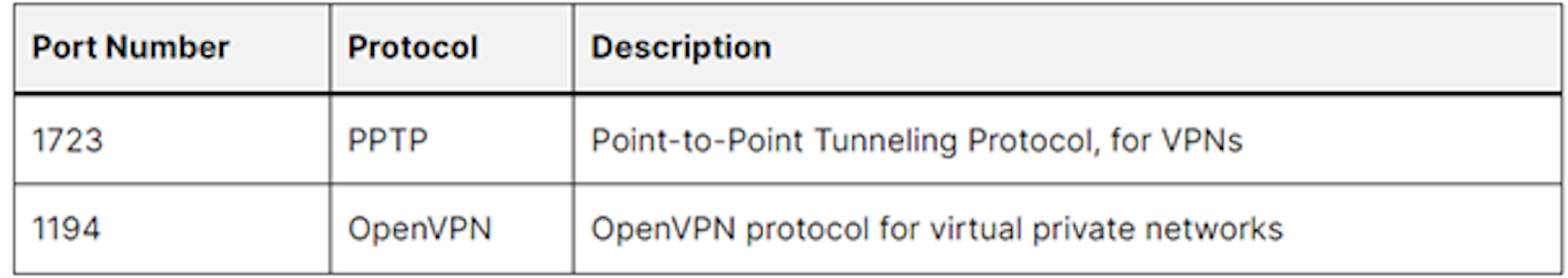
File Sharing and Collaboration Protocols
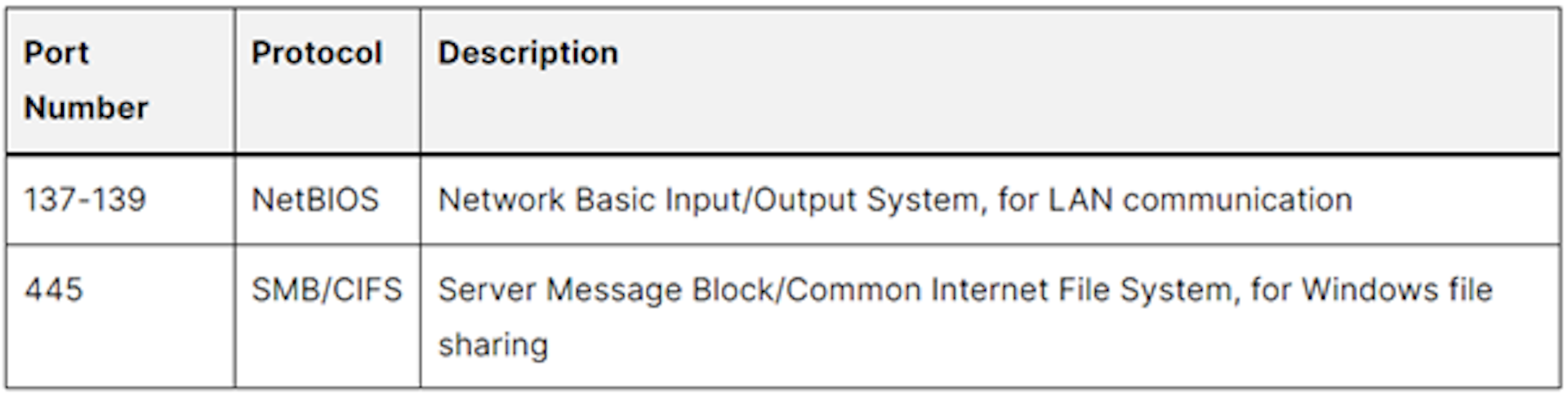
Security and Monitoring Protocols
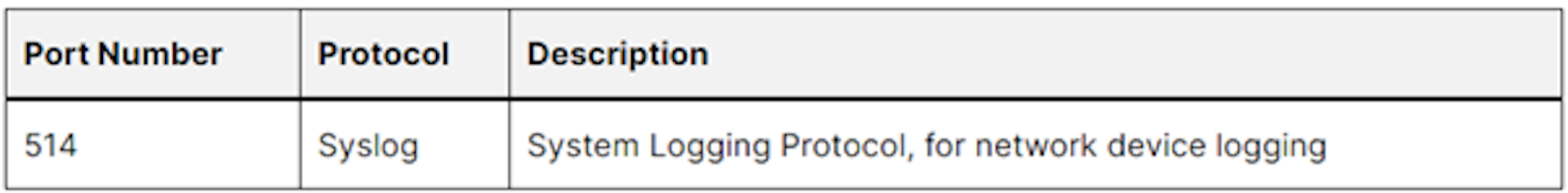
Please note that while these port numbers are standard, they can be altered based on system configurations and needs.
Network Sniffing and Analysis
Now, let's don our detective hats and delve into network sniffing and analysis. It's like becoming a digital Sherlock Holmes, eavesdropping on computer conversations. Intrigued? Let's continue.
Network Sniffing: Unveiling Conversations
Imagine a bustling room where everyone's talking. Network sniffing lets us tune into specific conversations, deciphering meanings within the chatter.
In ethical hacking, sniffing unveils data coursing through a network. It's a goldmine – from connected devices to potential security gaps.
Tools for Network Sniffing

"But how do we 'sniff'?" Excellent query! We've got handy tools.
Wireshark: Peek into the internet's core. It's like having X-ray vision for network data.
Tcpdump: The command-line classic. No frills, just data.
Analyzing the Data
Sniffing's one thing, but understanding the data? That's where the real magic happens. Analyzing network traffic is like solving a puzzle.
Pattern Recognition: Spot repeated login attempts – potential brute-force attacks.
Identifying Weaknesses: Unencrypted passwords, sensitive info – all under scrutiny.
It's All in the Details
Network sniffing isn't just about data collection; it's decoding data's significance. It reveals the big picture, spots threats, and aids network protection.
Remember, ethical hacking is our role. We use our abilities for good, so always ensure proper authorization before diving into network traffic.
Firewalls and Security Measures

Let's switch gears from offense to defense! Firewalls and security measures play a pivotal role in protecting networks.
Firewalls: Guarding the Gates
Imagine a sturdy gate, permitting only authorized entry while thwarting intruders. A firewall does this for networks. It's the guardian – filtering what enters and exits a system.
Understanding firewalls equips ethical hackers against them and empowers system security. It's a win-win!
Types of Firewalls
Firewalls come in various types, each with a distinct approach. Like music genres, they have their rhythm and rules.
Packet Filtering Firewalls: These are like club bouncers, inspecting packet IDs (source IP, destination IP, port numbers, etc.) before granting access.
Stateful Inspection Firewalls: Smarter, they remember past packets, like an elephant never forgetting a face.
Proxy Firewalls: Middlemen ensuring no direct contact occurs between sides.
Additional Security Measures
Beyond firewalls, other security measures are in play. Intrusion detection systems (IDS), intrusion prevention systems (IPS), and honeypots (decoy systems) are part of network security's intriguing world.
Protect and Serve
Ethical hackers, our mission is protection and service. Identifying vulnerabilities, yes, but also fixing them. Grasping firewalls and security measures is essential in achieving that mission.
Conclusion
As our exploration of ports, protocols, and networking nears its conclusion, it is imperative to recognize that this is but one facet within the extensive realm of ethical hacking.
We, as digital explorers, are dedicated to comprehending, safeguarding, and enhancing the intricate networks upon which our modern world depends. Each morsel of knowledge acquired, and each skill honed, propels us toward this noble objective.
The comprehension of ports and protocols transcends mere understanding of how networks communicate; it entails a mastery of the internet’s language, an unspoken dialogue unfolding ceaselessly across innumerable devices.