Understanding SIEM, Microsoft Sentinel: Working, Merits and Demerits
Delve into SIEM & Microsoft Sentinel: Learn Functions, Advantages, and Drawbacks in Comprehensive Detail for Effective Security Operations.
Sehran Rasool janJanuary 8, 2024

Azure Overview
Microsoft Azure is a cloud platform, similar to others like AWS, Google Cloud, and Oracle. It provides various cloud solutions such as IaaS, PaaS, and SaaS.
What makes Microsoft Azure unique is its strong integration with many Microsoft products and services. This makes it a great choice for organizations that use Microsoft technologies. It's especially good for apps and services that work on Windows.
What is SIEM?
SIEM, an acronym for Security Information Event Management, is composed of two integral parts: SIM and SEM.
Security Information Management (SIM): involves the collection and storage of data from diverse sources, including logs from network and security devices, operating systems, applications, and other systems. This data is aggregated and normalized to provide a centralized view of security-related information.
Security Event Management (SEM): concentrates on the real-time analysis of security events and alerts generated by the collected data. Its role is to identify potential security incidents and generate alerts or notifications when suspicious or malicious activity is detected.
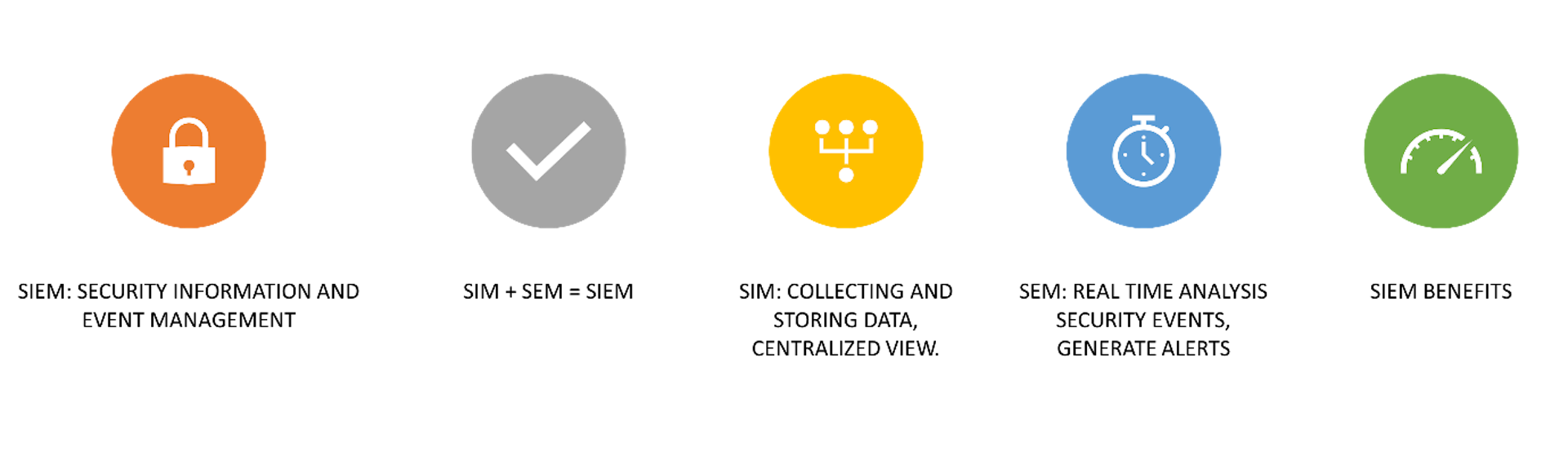
Benefits of SIEM
- Improved Efficiency: By combining SIM and SEM into a unified SIEM platform, organizations can reduce complexity, eliminate silos of data, and improve overall security operations efficiency.
- Efficient Threat Detection: Enhances security by quickly identifying and responding to potential threats.
- Comprehensive Security Visibility: SIEM Provides a holistic view of an organization's security environment.
What is Microsoft Sentinel
Microsoft Sentinel, is a cloud-based security information and event management (SIEM) system that helps organizations monitor and protect their digital environment by collecting, analysing, and responding to security data from various sources.
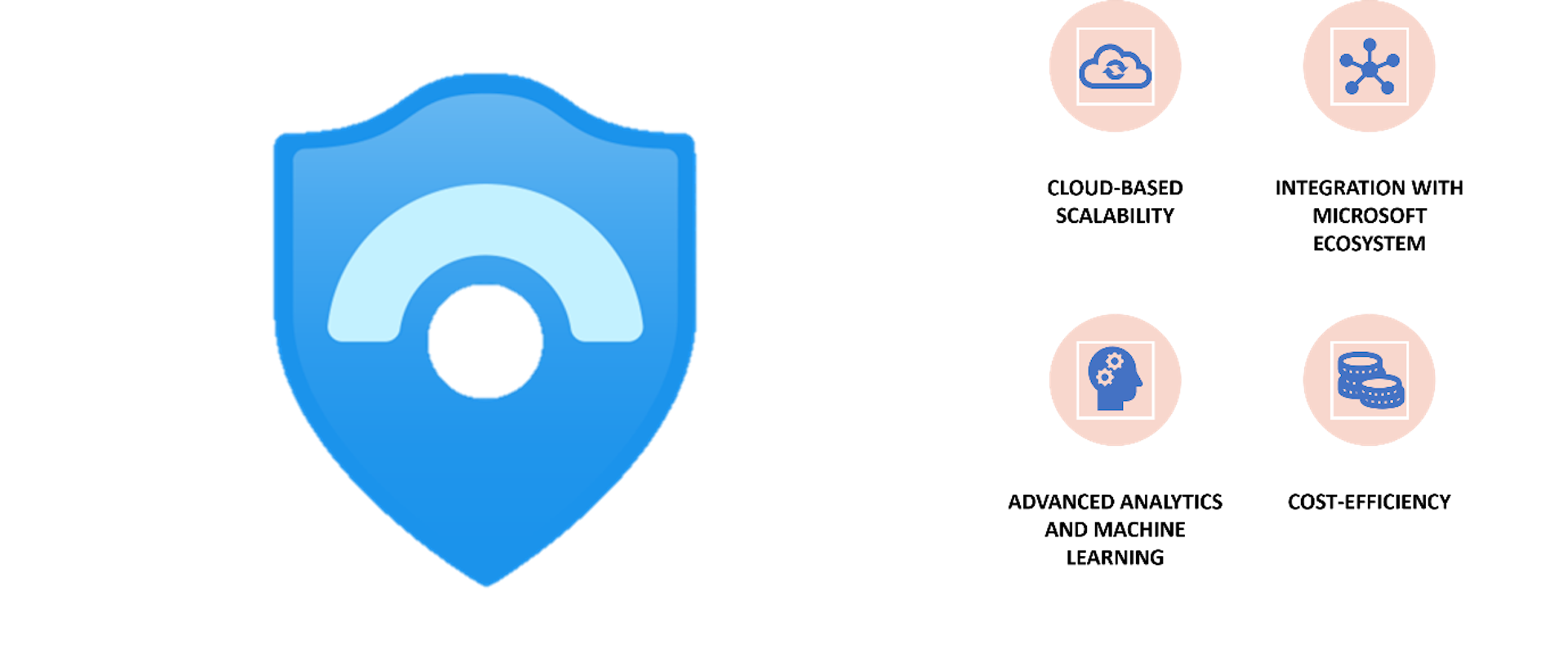
Cloud-Based Scalability: Microsoft Sentinel is a cloud-native solution, which means it can effortlessly scale to handle large volumes of security data. Traditional SIEM systems may require significant infrastructure investments to achieve similar scalability.
Integration with Microsoft Ecosystem: Sentinel integrates with other Microsoft security tools and services, such as Azure Security Center and Microsoft 365 Defender, creating a unified and wellcoordinated security ecosystem. Which a simple SIEM may lack with this level of integration.
Advanced Analytics and Machine Learning: Microsoft Sentinel helps us with advanced analytics and machine learning to detect and respond to security threats. Many traditional SIEM solutions may not have as advanced analytics capabilities.
Cost-Efficiency: Microsoft Sentinel being a cloud-based service, organizations can often achieve costefficiency because here we can go with Pay As Per Use Model ,But in traditional SIEM solutions we require substantial upfront hardware and software investments.
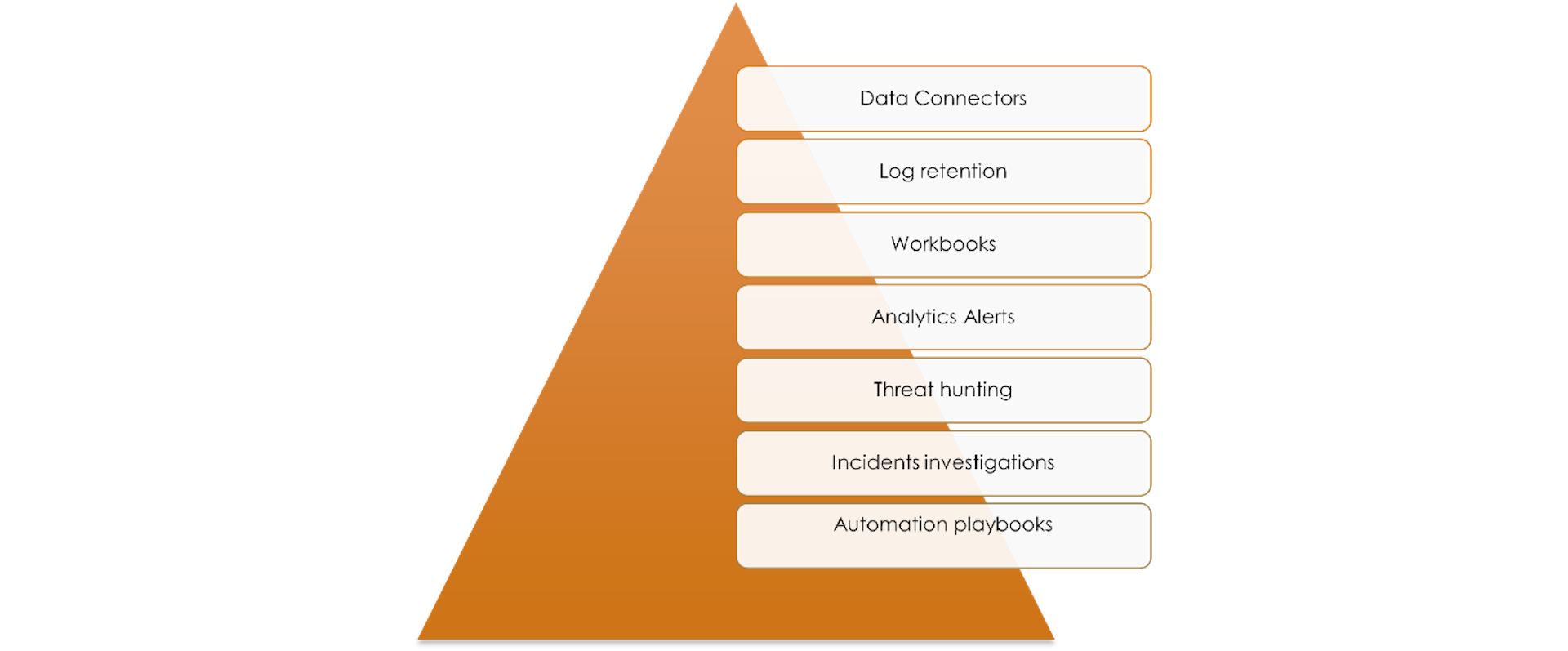
Working of Microsoft Sentinel
1.Data connectors
The first thing to do is to have your data ingested into Microsoft Sentinel. Data connectors let you do just that. You can effortlessly include certain services, like Azure activity logs, with a simple button selection.. Others, such as syslog, require a little configuration. There are data connectors that cover all scenarios and sources, including but not limited to:
- syslog
- Common Event Format (CEF)
- Trusted Automated exchange of Indicator Information (TAXII)
- Azure
- AWS services
2.Log retention
Once your data is ingested into Microsoft Sentinel, it is stored using Log Analytics.. The benefits of using Log Analytics include the ability to use the Kusto Query Language (KQL) to query your data. KQL is a rich query language that gives you the power to dive into and gain insights from our data.
3.Workbooks
Workbooks in Microsoft Sentinel serve as customizable, interactive reports that provide insights into your security data. They offer a user-friendly way to visualize and analyze information, allowing security professionals to gain a comprehensive understanding of their organization's security posture.
4.Analytics alerts
At present, our data ingestion process, facilitated by data connectors, has been efficiently executed. We've implemented log retention strategies to ensure a systematic approach to handling data over time. The visual representation of this data has been achieved through the utilization of workbooks, providing an intuitive and informative display.
Within this framework, the analytics functionality plays a pivotal role by generating alerts when potential security threats or suspicious activities are detected. It's noteworthy that the alerts are a culmination of both user-defined parameters, allowing for customization based on specific security criteria, and artificial intelligence-generated alerts that leverage advanced algorithms to identify anomalies and potential risks autonomously.
5.Threat hunting
In Microsoft Sentinel, there are ready-to-use Threat Hunting queries available for SOC analysts. As a SOC analyst, you can also create your own queries for more control over data analysis. Moreover, Microsoft Sentinel can be integrated with Notebooks, which comes in handy during complex investigations. This integration enhances your investigative capabilities with machine learning, visualizations, and in-depth data analysis. It's a valuable tool for making security activities more effective.
6.Incidents and investigations
An incident gets generated when an alert, which you've set up, goes off. In Microsoft Sentinel, you can handle standard incident management duties, such as adjusting the status or assigning incidents to specific individuals for investigation. Microsoft Sentinel goes a step further with its investigation functionality, allowing you to visually explore incidents by mapping entities across log data along a timeline.
7.Automation playbooks
Automation Playbooks in Microsoft Sentinel are predefined workflows designed to automate and orchestrate responses to security incidents. These playbooks execute a series of automated actions, such as querying additional data, isolating affected devices, blocking malicious IPs, and sending notifications, in a specific sequence. The purpose is to streamline incident response, reduce manual intervention, and enhance the efficiency of security operations. Customizable to specific security needs, Automation Playbooks ensure a consistent and rapid response, contributing to an overall strengthened security posture for organizations using Microsoft Sentinel.
Merits and Demerits of Microsoft Sentinel
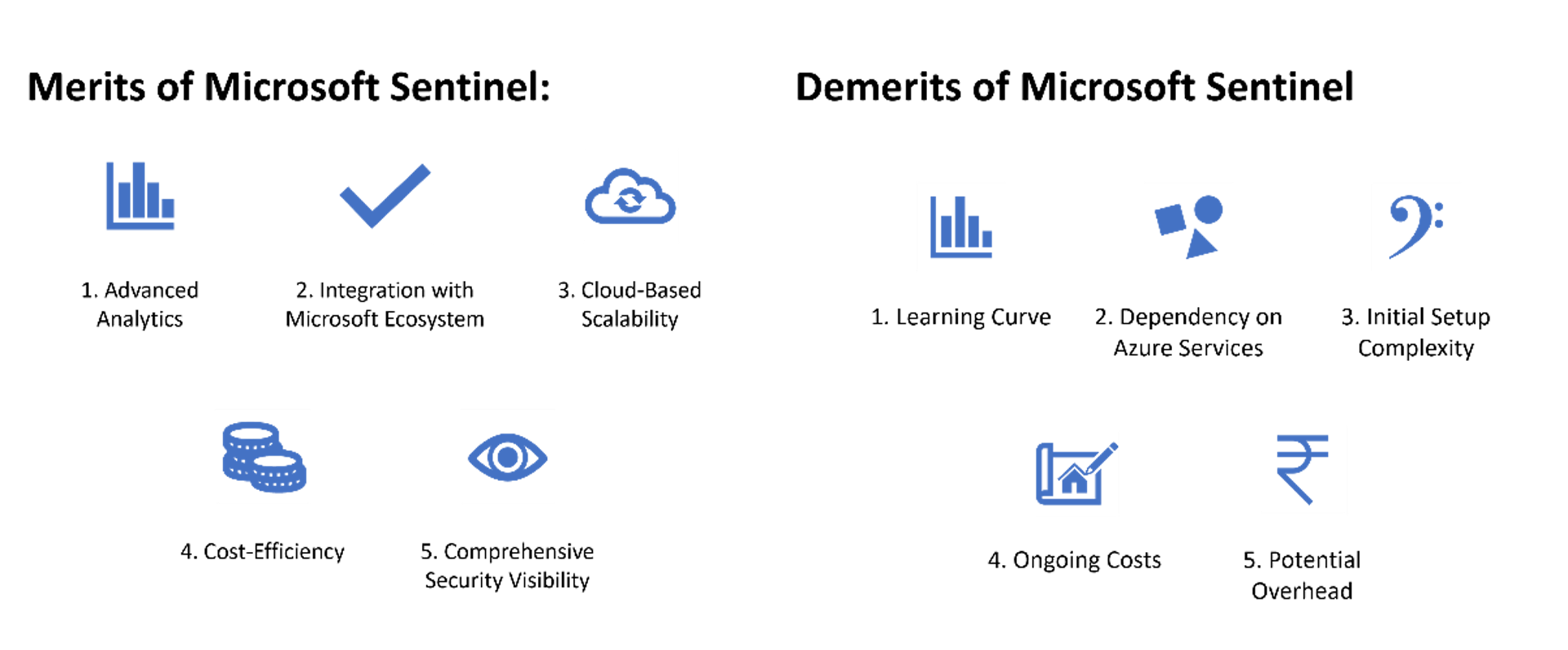
Merits of Microsoft Sentinel:
- Advanced Analytics: Leverages advanced analytics and machine learning for enhanced threat detection and response.
- Integration with Microsoft Ecosystem: Seamlessly integrates with various Microsoft security tools and services, creating a unified security ecosystem.
- Cloud-Based Scalability: Easily scales to handle large volumes of security data, offering flexibility and scalability.
- Cost-Efficiency: As a cloud-based service, follows a Pay-As-You-Go model, providing cost efficiency and avoiding substantial upfront investments.
- Comprehensive Security Visibility: Provides a holistic view of an organization's security environment, enabling thorough monitoring and protection.
Demerits of Microsoft Sentinel:
- Learning Curve: Implementing and fully utilizing Microsoft Sentinel may have a learning curve, especially for those unfamiliar with Azure and Microsoft technologies.
- Dependency on Azure Services: Organizations heavily invested in other cloud platforms may find adapting to Azure-centric solutions challenging.
- Initial Setup Complexity: Configuring data connectors and certain services may be complex initially, requiring careful planning and execution.
- Ongoing Costs: While the Pay-As-You-Go model can be cost-efficient, continuous usage may result in cumulative costs that need monitoring.
- Potential Overhead: Automation playbooks, while powerful, might introduce operational overhead, necessitating continuous refinement and maintenance.
Conclusion
Microsoft Azure Sentinel is a cloud-based security solution that seamlessly integrates with the Microsoft ecosystem, providing advanced analytics, cost-efficiency, and scalable security operations. It enables organizations to efficiently monitor and protect their digital environment while offering data connectors, log retention, and customizable workbooks for effective threat detection and response.