
Unveiling the Depths of BOTNETs
Cyberspace encompasses the vast interconnected network of computers and devices known as the internet. However, in this dynamic digital landscape, questions arise about our actual security. Amid daily internet use, are websites truly safe from threats? As cybercriminals employ extensive bot armies or botnets, the persistent profitability of older methods cannot be ignored.
Security
The term 'cyberspace' refers to the intricate network of interconnected computers, devices, and networks constituting the internet. Yet, amidst this dynamic digital landscape, can we claim true security? Are the websites we engage with daily truly impervious to threats? Do we give due thought to data security as we navigate the virtual realm? While the realm of cybercriminal activities thrives, we cannot disregard the persistent profitability of older ventures. Criminals Employ Vast Bot Armies, Referred to as Botnets, to Magnify the Scope of Their Activities.
One notorious botnet, Emotet, stands out for its devastating impact on multiple organizations. Originally detected in 2014 when ransomware attacks primarily targeted financial institutions, Emotet initially operated as a banking Trojan. However, over time, it morphed into a sophisticated botnet disseminating various forms of malware. Emotet's attack strategy, though seemingly straightforward, enabled it to evade cyber defenses effectively. It spread through phishing campaigns housing malicious Excel or Word documents. This malware leveraged spam emails to infiltrate systems, often marketed as part of the infamous Malware-as-a-Service (MAAS) program. To curb the potential damage of botnets capable of compromising devices and data, implementing robust control measures is essential. While eradicating such attacks might remain a challenge, safeguarding our devices and data from their clutches is within reach.
Understanding Botnets?
At its core, a botnet signifies a network of robotic entities. Often termed as a 'zombie army,' it entails computers manipulated without the owners' knowledge. A cluster of malware-infected computers, under the command of a single attacker, constitutes a 'bot-herd.' Though the term 'bot' typically denotes automated actions devoid of user intervention, it has recently taken on a more sinister connotation, encompassing novel hacking-related risks.
Computers enlisted in the zombie army often circumvent effective firewalls and security measures. These bots can emerge through dormant Trojan horse programs, awaiting activation, or by exploiting open internet ports on host computers. A botnet controller dispatches commands to potential bots through Trojan or malicious software from an Internet Relay Chat (IRC) site. This methodology can trigger Distributed Denial of Service (D-DoS) attacks. In the Current Scenario, Botnet Attacks Proliferate, Utilizing Their Infrastructure to Spread Malware, Obtain Data, Infiltrate Systems, and Compromise Organizational Confidentiality.
To safeguard ourselves and our companies from the botnets while battling these gigantic malware-spreading bots, we must implement countermeasures.
Tactics Employed in Botnet Attacks
The first step is sending viruses, worms, spyware, or keyloggers through email spam or using different strategies where the victim can download malicious files or click the malicious links which leads to downloading the malware set up by attackers. Denial of distribution attack leverages the massive scale of the botnet to overload a target network or server with requests, rendering it inaccessible to its intended users. This kind of attack targets organizations for personal or political motives or to extort payment in exchange for ceasing the attack.
Stealing data involves personal or private data from the host PC, such as credit card numbers, bank credentials, and other sensitive personal information. Data is the most important part of the organization and stealing the most confidential data can bring more profit for the attackers. The motives of the hackers who build these botnets are simple they look for profit by any means of cyber-criminal activity. The financial breach includes botnets specifically designed for the direct theft of funds from enterprises and credit card information. Financial botnets, like the ZEUS botnet, have been responsible for attacks involving millions of dollars stolen directly from multiple enterprises over very short periods.
Click fraud is the technique used by fraudsters using bots to boost web ads by auto-clicking internet ads. Sometimes not going into suspicious websites are the best possible steps to protect our devices from botnets. A massive volume of the span can be generated using botnets, so they are called spambots. There are many advantages to using spambots, such as:
- Spammers can hide their identity.
- The spamming source becomes untraceable.
- The spamming process can be carried out with various other tasks and with high bandwidth.
- It sends spam emails with viruses attached.
- It can spread all types of malwares.
Smaller botnets are designed to compromise specific high-value systems of organizations from which attackers can penetrate and intrude further into the network. These intrusions are extremely dangerous to organizations as cybercriminals specifically target their most valuable assets, including financial data, research and development, intellectual property, and customer information.
The characteristics of the botnets can be defining as:
- A network of compromised autonomous machines.
- They can be controlled from a remote location.
- They are utilized for nefarious intentions.
Elements of a Botnet
The primary constituents of a botnet are typically two major components:
- Host Component: The bots within a botnet are the infected machines over which the botmaster exerts remote control. The bot-agent, a malicious program, facilitates this remote control, making it the host component of the botnet.
- Network Component: The network component of a botnet refers to the online resource harnessed by the botnet. Common purposes of a bot's network component include:
- (C&C) Command and control channel
- Malware distribution server
- Drop zone.
Architecture of Botnet
The initiator of a botnet (sometimes termed a 'bot herder' or 'bot master') can manage it remotely. The command protocols, which skilled botnet operators often construct from scratch, involve a server program, a client program for deployment, and a program embedding the client on the victim's computer. Bots typically operate surreptitiously, communicating with their Command and Control (C&C) server through covert channels like Twitter, IM, or the RFC 1459 (IRC) protocol. Newer bots might automatically scan their environment and exploit security vulnerabilities and weak credentials for spreading. The value of a bot within the botnet community often rises with its capacity to discover and propagate vulnerabilities. 'Scrumping' refers to exploiting a system's botnet connection to pilfer computer resources.
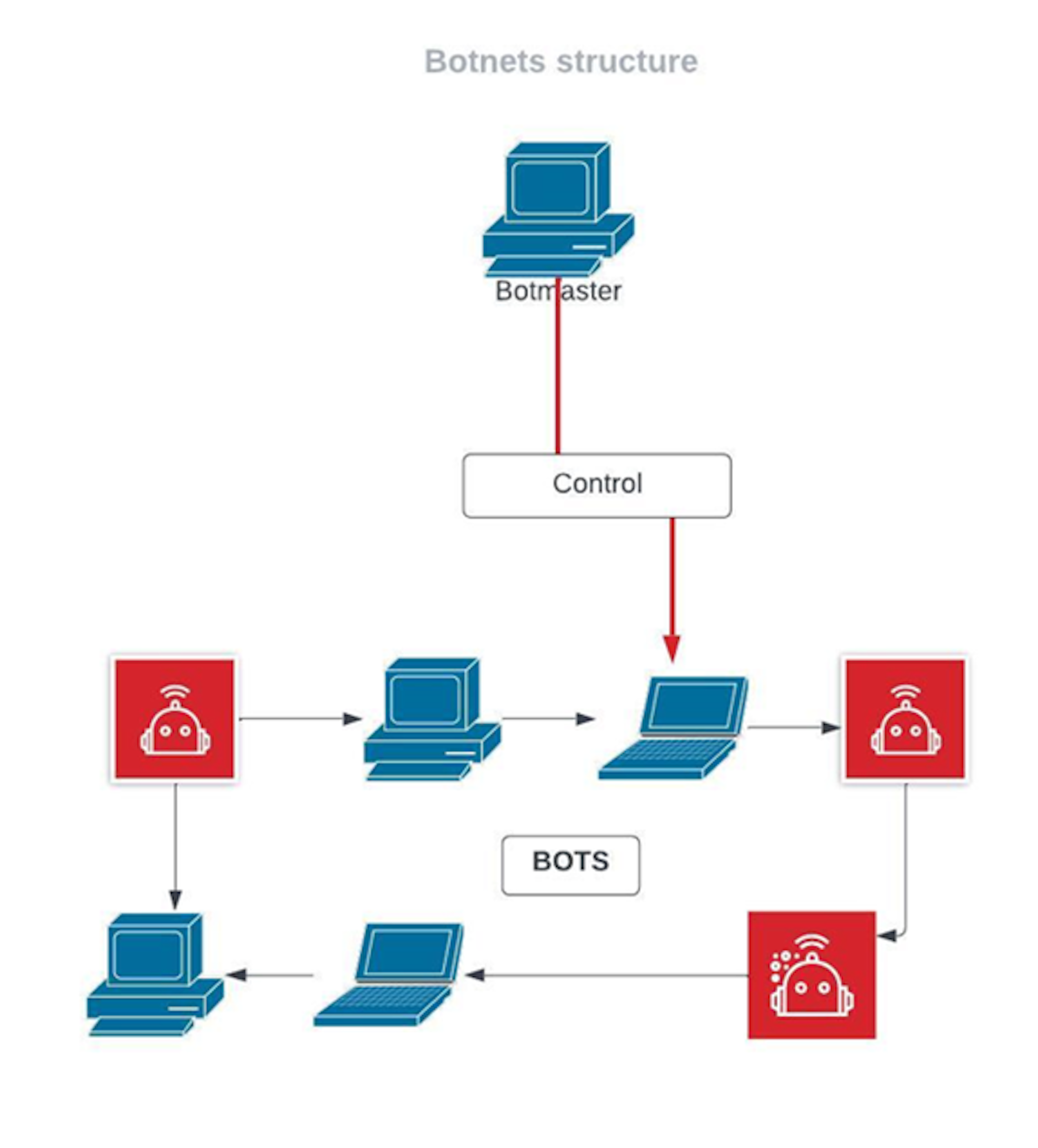
Some of the Botnets attacks examples are:
- CONFICKER: The Confickerbonnet is still one of the biggest ones ever made, with over 10.5 million devices under its control at its peak in 2008. Conficker, a computer worm-style botnet, spread at astronomical speeds. Conficker had already cost millions in damage after infiltrating government networks throughout Europe and was ready to wreak havoc on the whole planet. The botnet, however, thankfully was never employed in a DDoS assault. There are currently thought to be 500,000 PCs worldwide that contain it.
- Gameover ZEUS: Gameover ZEUS, an encrypted P2P botnet that is a member of the ZEUS malware family, is well known for being used to steal the banking credentials of millions of victims. It was estimated that Gameover ZEUS had cost more than $100 million in losses by the time it was destroyed.
- MIRAI: The MIRAI botnet, which preys on Linux devices like routers and webcams, was revealed as the source of numerous well-known DDoS assaults in 2016. When they find any IoT devices online with default passwords, computers infected with MIRAI infect them.
- Meris: In September 2021, the Meris botnet detonated "botnet Twitter" by bombarding Yandex with a record-breaking 21.8 million requests per second. About 250,000 machines are part of the Meris botnet, which earlier this year also targeted web infrastructure company Cloudflare.
Key Measures for Protection:
Understanding the process of botnet attacks is essential but also at the same time protecting yourself from this kind of cyber threats is one of the most important steps. Some of the things you may need to do to protect yourself and your organization from botnet attacks:
- Stay updated: Ensuring regular software updates across assets is pivotal in thwarting botnet-related malware. Unaddressed software vulnerabilities often serve as entry points for cyber attackers. Exploit kits, targeting systems with outdated patches, perpetuate these vulnerabilities.
- Leverage Antivirus Tools: Employ antivirus tools equipped with signature detection and heuristic analysis. This combination detects behavioral patterns of polymorphic malware, enhancing system protection against evolving threats.
- Exercise Caution with Email: Botnets thrive on spam and phishing tactics. Approach email attachments and unfamiliar links with caution, as they may harbor malware.
- Implement Firewalls: Reliable firewalls detect anomalous network traffic resulting from malware interactions, curbing data theft and instructions from botnet operators.
- Steer Clear of Pirated Software: Abstain from using cracked applications that lack manufacturer support and security patches. Such applications are riddled with vulnerabilities that attackers exploit.
- Adopt Two-Factor Authentication (2FA): 2FA adds an extra layer of security against brute force attacks, a common vector for system infiltration.
- Embrace Least Privilege: Exercise caution with access rights. Restrict employees' access based on their roles to prevent lateral movement of malicious code.
- Continuous Vigilance: Stay informed about botnet developments and offensive mechanisms through reputable cybersecurity sources.
Defending Against Botnets as a SOC:
In the role of a Security Operations Center (SOC), certain critical tasks warrant attention:
- User Awareness: Educate users about botnet indicators, potential consequences, and response strategies. Informed users are more likely to recognize and appropriately address suspected phishing and botnet attacks.
- Attack Detection: Identifying botnets can be challenging, as attackers strive to remain undetected. Monitoring network ports can aid in detecting botnet-related activities.
- Isolate Infected Devices: SOC teams must promptly isolate infected devices, disconnecting them from the network, conducting malware scans, and initiating investigations to mitigate further damage.
- Investigate Attacks: In-depth investigation is crucial following an attack. SOC teams collect evidence, assess the extent of the incident, contain and remediate, and subsequently report to stakeholders.
- Remediate Attacks: Prompt remediation involves isolating infected devices, removing malware, patching vulnerabilities, monitoring for residual activity, and delivering user awareness training.
- Follow-Up and Learn: Post-incident reviews are essential. Identify areas for improvement, develop remediation plans, implement these plans, and continuously monitor for effectiveness.
- Blocklist Domains/IPs: Effectively blocklist domains and IP addresses linked to command-and-control servers. Prevent communication between compromised devices and attackers.
By carrying out these duties, the SOC may play a crucial part in shielding the company's consumers from the negative impacts of botnet assaults.
Conclusion:
Botnet attacks remain a formidable threat to individuals and organizations alike. A comprehensive understanding of these attacks, coupled with proactive protective measures, is paramount. Exercise caution with email communications, keep software up-to-date, deploy robust antivirus tools, and exercise prudence when interacting with unfamiliar links or files. By adhering to these guidelines, you can effectively shield yourself against botnet attacks and safeguard sensitive information."